Hundreds of Satisfied Clients | +30 Success Stories
We Accept Credit Card Payments

Software · Observability · Cybersecurity · Compliance
We are your nearshore technology partner specializing in software development, cybersecurity, observability and Compliance.
Cloud done the right way, the best practices way.
Software Development
Custom development using React and Django. Secure, scalable, and modern solutions aligned to your business needs.
Cybersecurity Services
From endpoint protection with Malwarebytes to incident response and SIEM integration, we protect your organization proactively.
Observability
Monitoring, logging, and alerting for mission-critical systems. Integrations with Datadog, AWS CloudWatch, and more.
Compliance
Trusted compliance specialists on demand. We deliver qualified professionals to strengthen your compliance program so you stay ahead of regulatory changes.


Cybersecurity
Autonomous Security, Without Complexity
Our cybersecurity services are designed to prevent, detect, and respond to modern threats. With Malwarebytes EDR, incident response playbooks, SIEM integration, and phishing simulations, we protect every endpoint and provide visibility into your attack surface.
Software
Built with React + Django, Scaled for Growth
We specialize in full-stack web applications using React and Django. Our team delivers clean, maintainable code aligned with DevOps best practices. Whether it’s internal tools or customer platforms, we build for performance and security from day one.

Observability
Make Your Systems Talk to You
With integrations like Datadog, we help you visualize your infrastructure, detect anomalies, and reduce downtime. We deploy logging, monitoring, and tracing strategies tailored to your tech stack — all tied to actionable alerts.
Compliance
Compliance Talent That Meets Demands
We provide qualified compliance professionals to support your evolving regulatory needs. From short-term advisory projects to long-term compliance management, our staffing solutions help you stay compliant and agile.

Our Certifications, Tools & Partners


Tailored Packages
Choose the right level of service based on your team size and needs. From startups to enterprise, we’ve got you covered.
Cybersecurity Plans
- Basic: EDR + basic policies.
- Intermediate: Adds incident response & Gmail security.
- Advanced: Dashboards, phishing sim, SIEM.
Observability Plans
- Basic: Uptime + simple dashboard.
- Intermediate: Custom dashboards, logs, alerts.
- Advanced: Predictive alerts + compliance.
AWS Support Plans
- Basic: Backups, IAM, monthly audit.
- Intermediate: Multi-env, alerts, tagging.
- Advanced: Weekly review, 24/7 support.
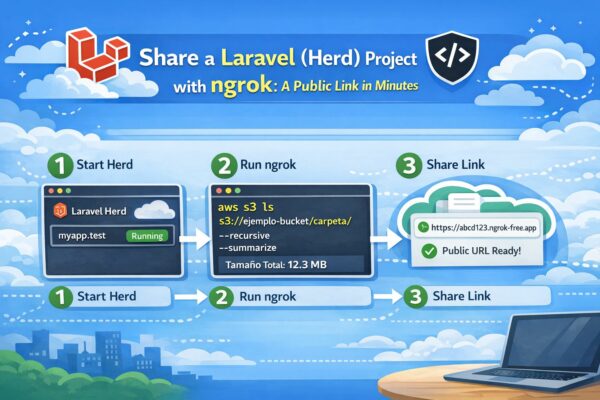
Share a Laravel (Herd) project with ngrok: a public link in minutes
Share a Laravel (Herd) project with ngrok: a public link in minutes If you’re running [...]
Feb
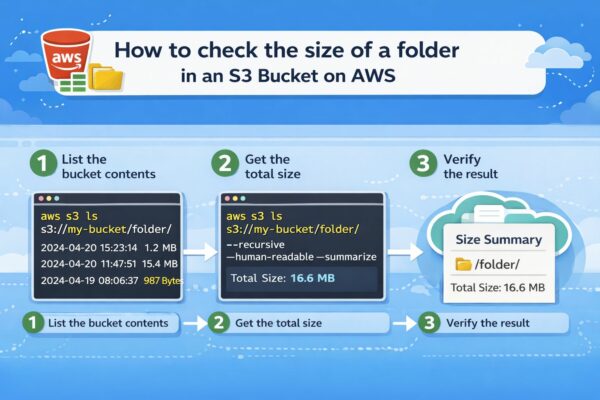
How to Calculate the Size of an S3 Folder Using AWS CLI
How to Calculate the Size of an S3 Folder Using AWS CLI Calculating the size [...]
Feb
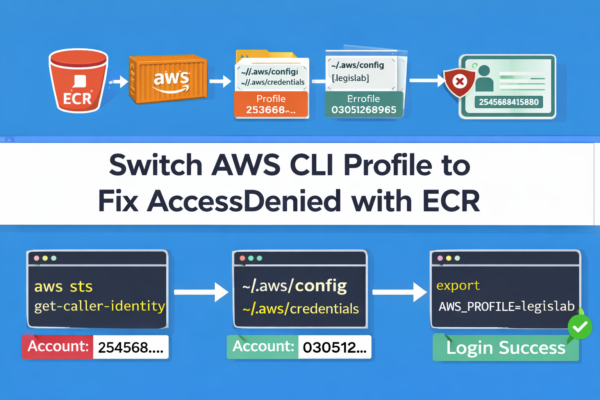
How to switch AWS CLI user/account (profiles) and fix “AccessDenied” in ECR
How to switch AWS CLI user/account (profiles) and fix “AccessDenied” in ECR If you use [...]
Feb
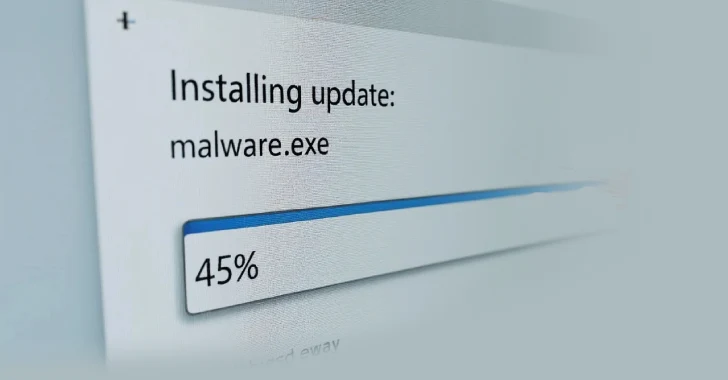
Akira Ransomware Continues Exploiting SonicWall Vulnerability Using Legitimate Tools
Security researchers warn that the Akira ransomware group is still actively exploiting a year-old SonicWall [...]
Sep
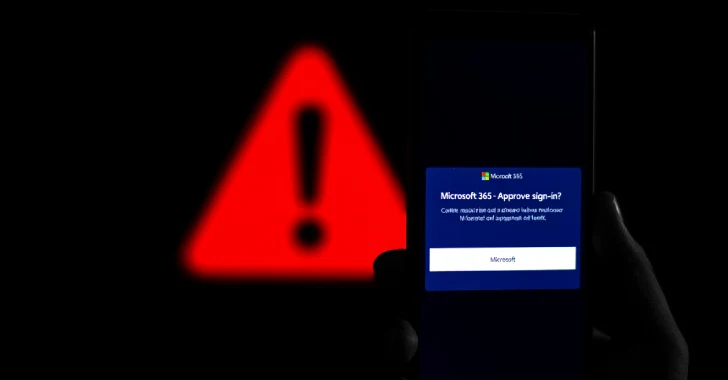
Microsoft Thwarts AI-Generated Phishing Campaign Targeting US Organizations
Microsoft Threat Intelligence recently intercepted a sophisticated phishing campaign that appears to have leveraged AI-generated [...]
Sep
How AI is Transforming Cyberattacks According to Wiz CTO Ami Luttwak
Ami Luttwak, chief technologist at cybersecurity firm Wiz, recently shared insights with TechCrunch on how [...]
Sep
First Malicious MCP Server Exposed in Rogue Postmark-MCP Package
Cybersecurity researchers have identified the first-ever case of a malicious Model Context Protocol (MCP) server [...]
Sep
Amazon Agrees to $2.5 Billion Settlement Over Prime Practices
Amazon has agreed to a $2.5 billion settlement with the Federal Trade Commission (FTC) following [...]
Sep
Cognex Industrial Camera Vulnerabilities Pose Risks Without Available Patches
Several industrial cameras produced by Cognex have been identified with serious security vulnerabilities, and the [...]
Sep
Jaguar Land Rover Initiates Phased Recovery Following Cyber-Attack
Jaguar Land Rover (JLR) has started a gradual restart of its operations after a significant [...]
Sep
Massive Exposure of Indian Bank Transfer Records After Cloud Security Misconfiguration
A recent data exposure incident has raised alarms in India’s financial sector, after hundreds of [...]
Sep
New COLDRIVER Campaign Uses ClickFix to Deliver Lightweight BAITSWITCH and SIMPLEFIX Malware
A Russia-linked advanced persistent threat (APT) tracked as COLDRIVER has been tied to a fresh [...]
Sep
Hackers Exploit Nursery Data Breach to Pressure Parents
Just when it seems cybercriminals cannot stoop any lower, a group proves otherwise. According to [...]
Sep
Chinese Cyberespionage Group RedNovember Targets Global Defense and Government Organizations
Cybersecurity firm Recorded Future has reported that a Chinese cyberespionage group, known as RedNovember, has [...]
Sep
Malicious AI Agent Server Found Exfiltrating Emails
Security researchers from Koi Security have uncovered a malicious update in a widely used Model [...]
Sep
Neon App Pays Users to Record Calls, Selling Data to AI Firms
A new social networking app called Neon Mobile has risen to become the No. 2 [...]
Sep
Salesforce Patches “ForcedLeak” Vulnerability That Exposed CRM Data Through AI Prompt Injection
A newly disclosed critical security flaw in Salesforce’s Agentforce platform could have allowed attackers to [...]
Sep
New SVG-Based Phishing Attack Shows Why These Files Can Be Dangerous
Cybercriminals are once again exploiting SVG (Scalable Vector Graphics) files in a new phishing campaign [...]
Sep
Hackers Breach Boyd Gaming Systems
Boyd Gaming, a prominent casino and entertainment company, has reported a cybersecurity breach impacting some [...]
Sep
Cell Tower Hacking Equipment Seized Ahead of UN General Assembly
The U.S. Secret Service has recently dismantled a network of electronic devices capable of disrupting [...]
Sep
How One Weak Password Brought Down a 158-Year-Old Company
Most businesses struggle to survive beyond their fifth year—statistics show that around half of small [...]
Sep
WhatsApp Rolls Out In-App Message Translation Feature
With more than 3 billion users across 180+ countries, WhatsApp continues to look for ways [...]
Sep
Police Deploying Drones as Flying License Plate Readers Raises Privacy Concerns
A recent report from the Electronic Frontier Foundation (EFF) warns that U.S. police departments are [...]
Sep
SolarWinds Issues Third Attempt to Patch Critical Web Help Desk Vulnerability
SolarWinds has announced a third hotfix for a remote code execution (RCE) vulnerability affecting its [...]
Sep
Deepfake Attacks Affect Nearly Two-Thirds of Organizations
A recent Gartner survey reveals that nearly 62% of organizations have experienced a deepfake attack [...]
Sep
European Airports Still Facing Disruptions After Ransomware Attack
A ransomware attack targeting Collins Aerospace, the company behind check-in systems for several European airports, [...]
Sep
Two New Supermicro BMC Vulnerabilities Enable Malicious Firmware to Bypass Root of Trust
Cybersecurity experts have revealed details of two newly discovered vulnerabilities affecting Supermicro Baseboard Management Controller [...]
Sep
Scammers Are Impersonating the FBI to Steal Sensitive Data
Cybercriminals are once again exploiting trust in government institutions—this time by setting up fake versions [...]
Sep
How to Secure AI Agents and Non-Human Identities in Your Organization
Modern enterprises are no longer just about human users. Behind the scenes, thousands of non-human [...]
Sep
Spike in Indeed Job Scam Texts Exploits Weak Job Market
Scammers are once again targeting job seekers with fraudulent text messages impersonating popular employment platforms [...]
Sep
Stellantis Confirms Customer Data Compromised in Security Breach
Stellantis, the multinational automotive company behind brands such as Chrysler, Fiat, Jeep, Dodge, and Ram, [...]
Sep
Russian State-Linked Hackers Collaborate on Cyberattacks Targeting Ukraine
A recent report from ESET reveals that two Russian state-associated cyber threat groups, Gamaredon and [...]
Sep
European Airports Hit by Ransomware Attack on Collins Aerospace
Several major airports across Europe experienced significant disruptions following a ransomware attack targeting Collins Aerospace, [...]
Sep
6 Browser-Based Threats Security Teams Must Address Today
The frequency and sophistication of attacks targeting web browsers have surged dramatically in recent years. [...]
Sep
Samsung Fixes Critical Zero-Day Vulnerability Exploited on Android Devices
Samsung has rolled out its September 2025 security updates addressing a critical zero-day vulnerability that [...]
Sep
Phishing Campaigns Exploit RMM Tools for Covert Remote Access
Security researchers are warning about a wave of phishing campaigns that deploy remote monitoring and [...]
Sep
Apple Raises the Stakes for Spyware Makers with New iPhone Security Feature
Amid the buzz of new product launches, Apple quietly unveiled a security upgrade for its [...]
Sep
AI-Powered “Villager” Pentest Framework Hits 11K PyPI Downloads, Raising Abuse Worries
A newly released AI-driven penetration-testing framework called Villager has amassed nearly 11,000 downloads on the [...]
Sep
Critical Vulnerability in DELMIA Apriso Factory Software Exploited in Attacks
Cybersecurity authorities have raised alarms over a critical vulnerability affecting DELMIA Apriso, a widely used [...]
Sep
France Reports Apple Warned Users About New Spyware Attacks
According to the French government, Apple has alerted several individuals that their devices may have [...]
Sep
Attackers Adopt Novel LOTL Techniques to Evade Detection
Threat actors are increasingly chaining living-off-the-land (LOTL) techniques and abusing less obvious file types to [...]
Sep
New HybridPetya Ransomware Bypasses UEFI Secure Boot via CVE-2024-7344
Cybersecurity researchers have uncovered a new ransomware strain called HybridPetya, which resembles the infamous Petya/NotPetya [...]
Sep
From a Simple “Like” to Financial Ruin: A Real-Life Scam Story
We often hear about people falling victim to scams, losing money, and facing devastating consequences. [...]
Sep
Akira Ransomware Exploits Year-Old SonicWall Vulnerability
Cybersecurity researchers have reported that the Akira ransomware group is actively exploiting a year-old vulnerability [...]
Sep
Fileless Malware Uses Legitimate Tools to Deploy Advanced RAT
Cybersecurity researchers have uncovered a sophisticated fileless malware campaign that leverages legitimate system tools to [...]
Sep
UK Students Drive Majority of School Cybersecurity Breaches, ICO Warns
The UK’s Information Commissioner’s Office (ICO) has revealed a concerning trend: students are responsible for [...]
Sep
Google Pixel 10 Introduces C2PA Support for Verifying AI-Generated Media
Google has announced that its new Pixel 10 smartphones will natively support the Coalition for [...]
Sep
Fake BMV Texts Target Victims With Phishing and Identity Theft
Cybercriminals are currently running a phishing campaign disguised as messages from the Bureau of Motor [...]
Sep
Microsoft Releases Patches for 86 Vulnerabilities in September 2025
Microsoft has rolled out its September 2025 Patch Tuesday updates, addressing a total of 86 [...]
Sep
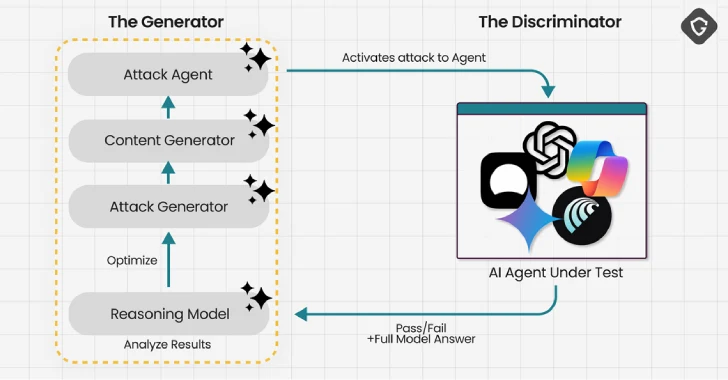
Threat Actor Accidentally Reveals AI-Powered Attack Methods
In a highly unusual incident, a threat actor inadvertently exposed their own operational methods and [...]
Sep
Plex Advises Users to Reset Passwords Following Data Breach
Media streaming service Plex has urged its users to update their account passwords after confirming [...]
Sep
RatOn: New Android Malware with NFC Relay and Banking Fraud Capabilities
A newly identified Android malware named RatOn has rapidly evolved from a simple tool for [...]
Sep
Ethical Hackers Uncover Major Vulnerabilities in RBI Platforms
Two ethical hackers recently revealed severe security flaws in the platforms operated by Restaurant Brands [...]
Sep
Noisy Bear Campaign Against Kazakhstan’s Energy Sector Revealed as Internal Phishing Exercise
A recently reported cyber campaign allegedly targeting Kazakhstan’s energy sector, initially linked to a threat [...]
Sep
AI-Powered Ransomware Is Becoming a Reality, PromptLock Remains a Prototype
Ransomware leveraging artificial intelligence is no longer a concept, though PromptLock, the recently discovered proof-of-concept [...]
Sep
MostereRAT Targets Windows Users with Advanced Evasion Techniques
Cybersecurity researchers have uncovered a phishing campaign distributing a new strain of malware called MostereRAT, [...]
Sep
Salesloft Links Drift Data Breaches to March GitHub Account Compromise
Salesloft has disclosed that a GitHub account breach in March allowed attackers to steal authentication [...]
Sep
GPUGate Malware Exploits Google Ads and Fake GitHub Commits to Target IT Companies
Cybersecurity researchers have uncovered a sophisticated malvertising campaign that abuses Google Ads to deliver malware [...]
Sep
More Cybersecurity Firms Impacted by Salesforce–Salesloft Drift Breach
Several well-known cybersecurity companies — Proofpoint, SpyCloud, Tanium, and Tenable — have confirmed that their [...]
Sep
Bridgestone Responds to Cyber Incident Affecting North American Facilities
Bridgestone has confirmed it is addressing a cybersecurity incident that disrupted operations at several of [...]
Sep
Why X’s New Encrypted Chat Isn’t Ready for Trust
X, formerly known as Twitter, has begun rolling out its new encrypted messaging feature, branded [...]
Sep
CISA Urges Immediate Patching of Critical Sitecore Vulnerability Under Active Exploitation
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent directive requiring all [...]
Sep
Roblox Introduces Age Verification for Communication Features to Enhance Child Safety
Roblox, one of the world’s most popular platforms for creating, sharing, and playing 3D virtual [...]
Sep
Cato Networks Acquires AI Security Firm Aim Security to Strengthen SASE Platform
Secure Access Service Edge (SASE) leader Cato Networks has announced its first-ever acquisition with the [...]
Sep
Malicious npm Packages Exploit Ethereum Smart Contracts in Supply Chain Attack
A new malicious campaign has been uncovered targeting developers through npm packages and GitHub repositories, [...]
Sep
Iranian Hackers Exploit 100+ Embassy Email Accounts in Global Phishing Campaign
A hacking group with ties to Iran has been connected to a coordinated, multi-wave spear-phishing [...]
Sep
PayPal Users Targeted in Sophisticated Account Profile Scam
A new wave of phishing attacks is targeting PayPal users with emails that appear highly [...]
Sep
Cloudflare and Palo Alto Networks Impacted by Salesloft Drift Breach
Cloudflare and Palo Alto Networks have confirmed that their Salesforce environments were accessed by threat [...]
Sep
Shadow AI Discovery: The New Frontier in Enterprise Governance
The Reality of AI AdoptionRecent studies reveal a striking contrast between corporate adoption plans and [...]
Sep
Cloudflare Mitigates Record-Breaking 11.5 Tbps DDoS Attack
Cloudflare has announced that it successfully mitigated the largest distributed denial-of-service (DDoS) attack ever recorded, [...]
Sep
Azure AD Credentials Found Exposed in Public Configuration File
A recent cybersecurity investigation revealed a critical vulnerability tied to Azure Active Directory (Azure AD), [...]
Sep
Hidden Connections and Security Risks Found in Popular VPN Apps
A recent investigation has revealed that more than 20 VPN applications available on the Google [...]
Sep
Lazarus Group Expands Arsenal With New Malware Strains PondRAT, ThemeForestRAT, and RemotePE
The North Korea-linked cybercriminal organization Lazarus Group has been connected to a sophisticated social engineering [...]
Sep
Google Confirms Workspace Accounts Impacted in Salesforce–Salesloft Drift Data Theft Campaign
Google has confirmed that a recent data theft campaign, which primarily targeted Salesforce customers through [...]
Sep
ScarCruft Deploys RokRAT Malware in Operation HanKook Phantom Targeting South Korean Academics
Cybersecurity researchers have uncovered a new phishing operation conducted by the North Korea-linked hacking group [...]
Sep
High-Risk SQL Injection Vulnerability Found in WordPress Membership Plugin
A critical security flaw has been identified in the WordPress Paid Membership Subscriptions plugin, a [...]
Sep
WhatsApp Addresses Zero-Click Spyware Exploit Targeting Apple Devices
WhatsApp announced on Friday that it has patched a critical security flaw in its iOS [...]
Sep
Android Droppers Expand Beyond Banking Trojans, Now Delivering SMS Stealers and Spyware
Cybersecurity experts have identified a new shift in the Android malware ecosystem, where dropper apps—traditionally [...]
Sep
Law Enforcement Dismantles VerifTools Fake ID Marketplace
Authorities in the United States and the Netherlands have successfully taken down VerifTools, a major [...]
Aug
North Korean Hackers Exploit Seoul Intelligence Files in Targeted Cyberattacks
A new large-scale spear-phishing campaign has been uncovered, targeting South Korean government officials and intelligence [...]
Aug
Nevada Confirms Ransomware Attack Behind Statewide Service Disruptions
Nevada officials have confirmed that the recent, days-long disruption of state services was the result [...]
Aug
Amazon Disrupts APT29 Watering Hole Campaign Exploiting Microsoft Device Code Authentication
Amazon has announced that it successfully identified and disrupted a watering hole campaign attributed to [...]
Aug
Netherlands Confirms Salt Typhoon Targeted Small Dutch Telecom Providers
Dutch intelligence services have confirmed that the Chinese-backed hacking group Salt Typhoon has carried out [...]
Aug
China’s “Salt Typhoon” Hackers Exposed After Years of Global Espionage
A China-linked advanced persistent threat (APT) group known as Salt Typhoon has been quietly compromising [...]
Aug
Fake IT Support Attacks Exploit Microsoft Teams to Spread Malware
A new phishing campaign targeting Microsoft Teams has been uncovered, where attackers impersonate IT support [...]
Aug
TransUnion Confirms Data Breach Exposing 4.4 Million Customers’ Personal Information
TransUnion, one of the largest credit reporting agencies in the United States, has confirmed a [...]
Aug
Malicious Nx Packages Exploited in ‘s1ngularity’ Supply Chain Attack, Leaking 2,349 Secrets
The maintainers of the popular Nx build system have disclosed a major supply chain attack [...]
Aug
Claude AI Exploited in Large-Scale Cybercrime Operation
Anthropic, the company behind the well-known AI coding assistant Claude, has revealed that the chatbot [...]
Aug
Salesloft OAuth Breach via Drift AI Chat Agent Exposes Salesforce Customer Data
A significant data theft campaign has targeted the Salesloft sales automation platform, exploiting OAuth and [...]
Aug
PromptLock: The First AI-Powered Ransomware Proof-of-Concept
Cybersecurity researchers have identified the first known ransomware family leveraging artificial intelligence for its local [...]
Aug
ShadowSilk Campaign Targets Central Asian Governments
A new wave of cyberattacks is making headlines, with researchers linking a campaign called ShadowSilk [...]
Aug
Anthropic Thwarts AI-Powered Cyberattack Campaign Automating Theft and Extortion
Anthropic announced that it successfully disrupted a highly sophisticated cyber operation in July 2025, where [...]
Aug
Another Security Flaw in TheTruthSpy Exposes Victims’ Data
TheTruthSpy, an infamous Android-based stalkerware, has once again come under scrutiny after a new vulnerability [...]
Aug
Critical Docker Desktop Vulnerability Allows Host Takeover
A serious security flaw in Docker Desktop has been discovered that allows attackers to gain [...]
Aug
Global Phishing Campaign Uses UpCrypter to Deploy Remote Access Tools
A large-scale phishing operation has been uncovered by cybersecurity researchers, leveraging highly personalized emails and [...]
Aug
Farmers Insurance Reports Data Breach Impacting Over 1 Million Customers
Farmers Insurance has confirmed a significant data breach after a third-party cyberattack exposed the personal [...]
Aug
MixShell Malware Delivered Through Contact Forms Targets U.S. Supply Chain Manufacturers
Cybersecurity experts have uncovered a sophisticated social engineering campaign aimed at U.S. manufacturing companies critical [...]
Aug
AI Browsers and the Hidden Threat of Prompt Injection
As AI-driven web browsers gain popularity, cybersecurity experts are warning about a rising threat known [...]
Aug
Chinese State-Sponsored Hackers Silk Typhoon Escalate Attacks on North American Industries
Cybersecurity researchers report that the Chinese state-sponsored hacking group Silk Typhoon is intensifying attacks on [...]
Aug
Attackers Exploit Virtual Private Servers to Target SaaS Accounts
Cybersecurity firm Darktrace has reported a rising trend where attackers leverage virtual private servers (VPS) [...]
Aug
Hackers Exploit New Method to Steal Microsoft Login Credentials
Microsoft users should stay vigilant: cybercriminals have developed a new phishing technique to capture login [...]
Aug
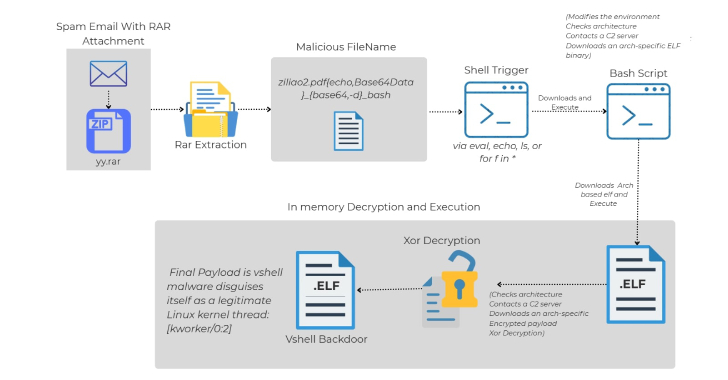
Linux Malware Exploits Malicious RAR Filenames to Evade Antivirus Detection
Cybersecurity researchers have identified a sophisticated Linux malware delivery method that leverages phishing emails and [...]
Aug
Grok Chats Found in Google Searches: A New Warning for AI Privacy
The conversation around artificial intelligence and privacy feels like it’s on repeat: once again, a [...]
Aug
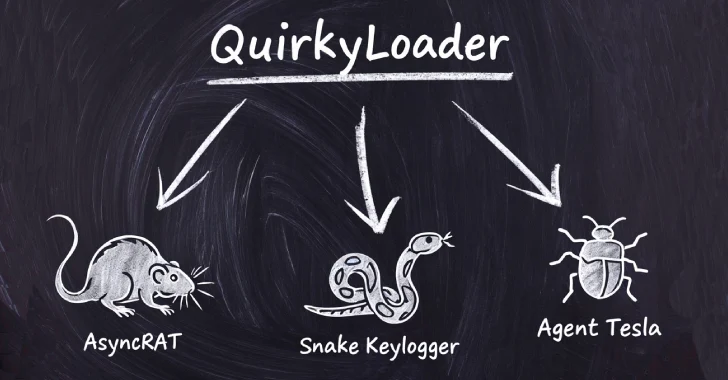
Hackers Exploit New QuirkyLoader Malware to Deploy Agent Tesla, AsyncRAT, and Snake Keylogger
ybersecurity experts have recently uncovered a new malware loader, dubbed QuirkyLoader, that has been actively [...]
Aug
Password Managers Exposed to Clickjacking Threats: Research Reveals Vulnerabilities
A recent study has uncovered that many popular password managers are at risk of clickjacking [...]
Aug
Colt Confirms Possible Customer Data Breach After Cyber Attack
Colt Technology Services has acknowledged that sensitive customer data may have been accessed and is [...]
Aug
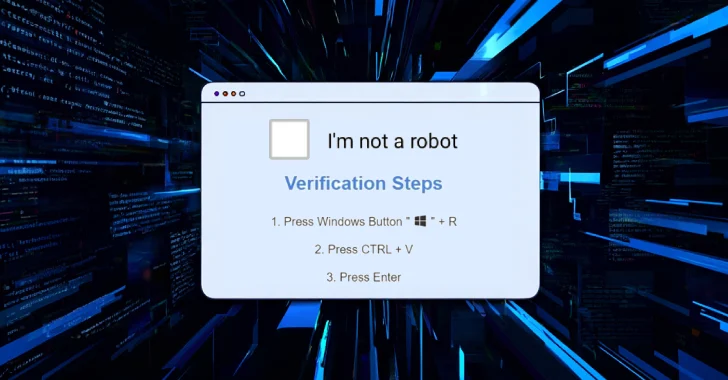
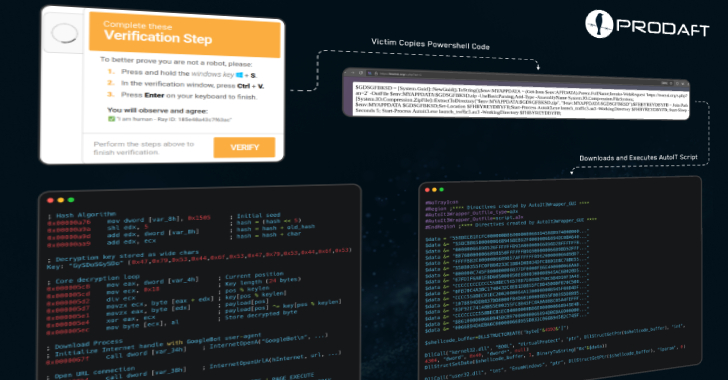
Cybercriminals Exploit ClickFix Tactic and Fake CAPTCHA Pages to Deploy CORNFLAKE.V3 Backdoor
Cybercriminals continue to refine their social engineering tactics, with recent campaigns leveraging fake CAPTCHA pages [...]
Aug
Google Reaches $30 Million Settlement in YouTube Child Privacy Case
August 21, 2025 – Google has agreed to a $30 million settlement in the United [...]
Aug
GPT-5 Faces Vulnerability: Router Can Redirect Queries to Older, Less Secure Models
A newly discovered vulnerability in GPT-5 could redirect user queries from the advanced GPT-5 Pro [...]
Aug
Inotiv Confirms Ransomware Attack Affecting Key Systems and Data
Inotiv, a pharmaceutical research company based in Indiana, has confirmed that it suffered a ransomware [...]
Aug
UAE-Based Startup Offers Up to $20 Million for Zero-Day Exploits Targeting Smartphones
A new cybersecurity startup based in the United Arab Emirates, Advanced Security Solutions, has entered [...]
Aug
PromptFix Exploit: How AI Browsers Are Being Tricked into Hidden Malicious Actions
Cybersecurity researchers have uncovered a novel attack method known as PromptFix, a prompt injection exploit [...]
Aug
Mule Operators in META Region Evolve Into Complex Fraud Networks
Fraud activity across the Middle East, Turkey, and Africa (META) is entering a new phase [...]
Aug
TPG Telecom Investigates iiNet Data Breach Impacting Thousands of Customers
August 19, 2025 – TPG Telecom, one of Australia’s leading providers of mobile voice and [...]
Aug
Allianz Life Data Breach Compromises 1.1 Million Customer Records
A recent cyberattack against Allianz Life has exposed the personal data of approximately 1.1 million [...]
Aug
UK Withdraws Apple Backdoor Demand After US Negotiations
The United Kingdom has officially withdrawn its request for a special “backdoor” into Apple’s cloud [...]
Aug
New GodRAT Trojan Targets Financial Trading Firms with Steganography and Gh0st RAT Code
A newly uncovered malware campaign is targeting financial institutions, particularly trading and brokerage firms, with [...]
Aug
AI-Powered Stuffed Animals: A Safer Alternative to Screen Time, or a Risk We Can’t Ignore?
Artificial Intelligence is rapidly reshaping the way we live, work, and even play. Now, it’s [...]
Aug
Microsoft Windows Flaw Exploited to Deploy PipeMagic Malware in RansomExx Attacks
Cybersecurity experts have revealed how threat actors have been exploiting a recently patched vulnerability in [...]
Aug
Chinese APT Targets Taiwanese Web Hosting Firms to Infiltrate High-Value Networks
Taiwan’s web hosting industry has recently come under sustained attack from a Chinese advanced persistent [...]
Aug
Popular npm Package “eslint-config-prettier” Compromised in Phishing Attack
A major supply chain security incident has been discovered involving the widely adopted npm package [...]
Aug
Workday Confirms Data Breach Involving Third-Party Database
August 18, 2025 – Workday, one of the world’s leading providers of human resources technology, [...]
Aug
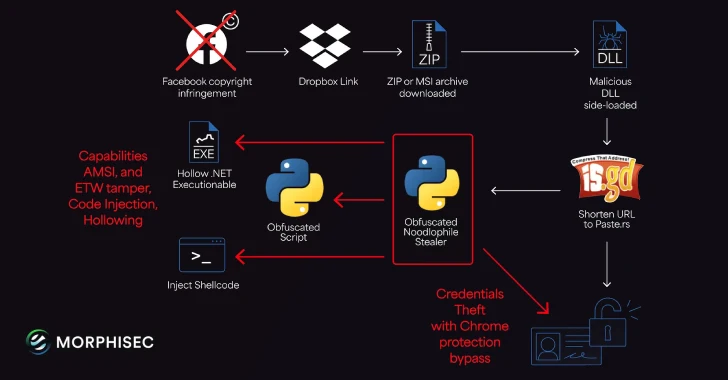
Noodlophile Malware Campaign Expands with Copyright-Themed Phishing Tactics
The operators behind the Noodlophile malware have broadened their global activities, using spear-phishing emails and [...]
Aug
Critical RCE Vulnerability Found in Cisco Secure Firewall Management Software
August 15, 2025 — Cisco has announced a severe security flaw in its Secure Firewall [...]
Aug
Zero Trust and AI: Redefining Privacy in the Era of Autonomous Agents
August 15, 2025 — Traditional views of privacy focused on control: walls, permissions, and access [...]
Aug
Italian Hotels Compromised, Tens of Thousands of Guest IDs Stolen and Sold Online
August 15, 2025 — Italy’s Computer Emergency Response Team (CERT-AGID) has issued a warning after [...]
Aug
U.S. Targets Garantex and Grinex Over $100M in Illicit Crypto Transactions Linked to Ransomware
August 15, 2025 — The U.S. Department of the Treasury’s Office of Foreign Assets Control [...]
Aug
Tight Budgets Push Cybersecurity Toward AI-Driven Automation
With financial constraints weighing heavily on cybersecurity teams, organizations are increasingly leaning on AI-powered automation [...]
Aug
Researchers Demonstrate Passkey Login Bypass Through WebAuthn Manipulation
Security researchers at SquareX, an enterprise browser security firm, have revealed a method that allows [...]
Aug
KernelSU v0.5.7 Vulnerability Allows Android Apps to Gain Root Privileges
Cybersecurity researchers have uncovered a critical flaw in KernelSU version 0.5.7 that could allow malicious [...]
New Android Malware Wave Targets Banking Customers with NFC Relay, Call Hijacking, and Root Exploits
Cybersecurity researchers have uncovered a new wave of Android malware, dubbed PhantomCard, which exploits near-field [...]
Aug
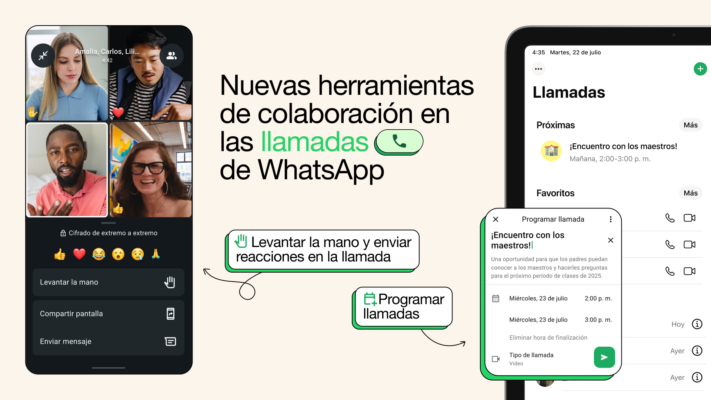
WhatsApp Introduces New Features for Smarter and More Interactive Group Calls
WhatsApp has rolled out new capabilities aimed at making group calls easier to schedule and [...]
Aug
Hackers Leverage CrossC2 to Bring Cobalt Strike Beacon to Linux and macOS
August 14, 2025 – Japan’s Computer Emergency Response Team Coordination Center (JPCERT/CC) has disclosed a [...]
Aug
Adobe Addresses Over 60 Security Vulnerabilities in August 2025 Patch Updates
August 13, 2025 – Adobe has released its August Patch Tuesday security updates, resolving more [...]
Aug
Deepfake AI Trading Scams Target Investors Worldwide
A recent investigation has uncovered a growing wave of fraudulent “AI-driven” trading platforms leveraging deepfake [...]
Aug
How We Discovered TeaOnHer Leaking Thousands of Users’ IDs in Under 10 Minutes
In a twist of irony, a dating gossip app called TeaOnHer—designed for men to share [...]
Aug
New PS1Bot Malware Campaign Leverages Malvertising for Multi-Stage In-Memory Attacks
A newly uncovered malvertising campaign is delivering a sophisticated, modular malware framework known as PS1Bot, [...]
Aug
Fortinet Issues Critical Warning on FortiSIEM Vulnerability (CVE-2025-25256) Amid Active Exploitation
August 13, 2025 — Fortinet has released a critical security advisory concerning a severe vulnerability [...]
Aug
Researcher Awarded $250,000 for Discovering Critical Chrome Sandbox Escape Vulnerability
A security researcher has secured the top payout in Google’s Chrome bug bounty program after [...]
Aug
Android’s pKVM Achieves Historic SESIP Level 5 Security Certification
Google has announced a major milestone in open-source security, with the Protected KVM (pKVM) hypervisor—integral [...]
Aug
New Storytelling Technique Circumvents GPT-5 Safety Mechanisms
Security researchers have identified a novel method capable of bypassing GPT-5’s built-in safeguards, enabling the [...]
Aug
ShinyHunters and Scattered Spider Allegedly Collaborate in New Wave of Data Extortion Attacks
August 12, 2025 – A major shift in the cybercrime landscape may be unfolding as [...]
Aug
Beware of Fake “Amazon Safety Recall” Messages — It’s Likely a Scam
Cybercriminals are exploiting a familiar fear-based tactic to trick users into clicking malicious links — [...]
Aug
Connex Credit Union Data Breach Exposes Personal Information of 172,000 Individuals
One of Connecticut’s largest credit unions has disclosed a major data breach that may have [...]
Aug
RomCom Hackers Exploit New WinRAR Zero-Day Vulnerability
A recently uncovered vulnerability in WinRAR, tracked as CVE-2025-8088, has been actively exploited by the [...]
Aug
U.S. Authorities Dismantle Russian Ransomware Infrastructure, Seize $1 Million in Bitcoin
In a major international cybercrime operation, the U.S. Department of Justice has announced the takedown [...]
Aug
Hackers Bypass Microsoft Defender to Deploy Ransomware, Report Finds
A recent cybersecurity report reveals that Microsoft Defender, Windows’ built-in security tool, is facing a [...]
Aug
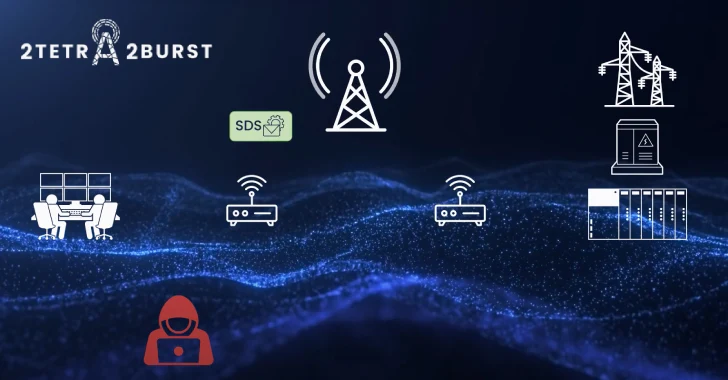
Newly Discovered TETRA Encryption Flaws Put Critical Communications at Risk
A new wave of security vulnerabilities has been uncovered in the Terrestrial Trunked Radio (TETRA) [...]
Aug
Columbia University Cyberattack Exposes Personal Data of Over 860,000 Individuals
Columbia University recently experienced a significant cyberattack that compromised the personal information of more than [...]
Aug
Malicious RubyGems and PyPI Packages Target Credentials and Cryptocurrency, Forcing Security Measures
A new wave of malicious software packages has been uncovered impacting two major software ecosystems: [...]
Aug
Australian Regulator Takes Legal Action Against Optus Following 2022 Data Breach Affecting Millions
The Australian Information Commissioner (AIC) has initiated civil proceedings against telecommunications provider Optus due to [...]
Aug
Instagram’s New Map Feature Triggers Privacy Concerns Over Location Sharing
Instagram’s recently introduced Map feature is drawing attention — and not for the reasons the [...]
Aug
AI Tools Power Brazilian Phishing Scheme as Efimer Trojan Targets 5,000 Crypto Users
Cybersecurity experts have uncovered a sophisticated phishing campaign in Brazil that exploits legitimate generative AI [...]
Aug
Organizations Urged to Patch Critical Microsoft Exchange Hybrid Vulnerability
Organizations operating hybrid Microsoft Exchange deployments have been alerted to a critical security vulnerability that [...]
Aug
Google Confirms It Was Targeted in Salesforce Data Breach Campaign
Google has acknowledged that it was among the companies affected by a broader data theft [...]
Aug
Massive Data Breach at Bouygues Telecom Exposes Information of 6.4 Million Customers
Bouygues Telecom, France’s third-largest mobile network operator, has disclosed a significant cybersecurity incident that compromised [...]
Aug
New Malicious Go and npm Packages Deliver Cross-Platform Malware and Enable Remote Data Wipes
Cybersecurity analysts have identified a new wave of supply chain threats involving malicious Go and [...]
Aug
Facebook Users Targeted in New Phishing Scam Using Mailto Links
Following a recent phishing campaign aimed at Instagram users, cybercriminals are now targeting Facebook accounts [...]
Aug
Microsoft Unveils Project Ire: Autonomous AI-Powered Malware Classification
On August 6, 2025, Microsoft introduced Project Ire, an autonomous AI system designed to analyze [...]
Aug
WhatsApp Removes 6.8 Million Fraudulent Accounts Tied to Global Scam Operations
Meta, the parent company of WhatsApp, has revealed it shut down 6.8 million accounts in [...]
Aug
DaVita Data Breach: Over 900,000 Patients Affected by Cyberattack Targeting Clinical Information
US-based kidney dialysis provider DaVita has disclosed a significant data breach that compromised sensitive personal [...]
Aug
Google Confirms Data Breach via Compromised Salesforce Database Linked to ShinyHunters Group
Google has confirmed a recent data breach that exposed contact details of some of its [...]
Aug
CISA Adds Three D-Link Vulnerabilities to KEV Catalog Amid Evidence of Active Exploitation
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has recently included three older security vulnerabilities [...]
Aug
Microsoft Introduces Project Ire: Autonomous AI Agent for Malware Detection
Microsoft has introduced a groundbreaking prototype known as Project Ire—an autonomous AI agent designed to [...]
Aug
Massive Smishing Campaigns Tied to Chinese Threat Actors Compromise Millions of US Payment Cards
A recently uncovered smishing campaign operated by Chinese cybercriminal syndicates may have compromised between 12.7 [...]
Aug
Cisco Hit by Vishing Attack That Exposed Customer Data
Cisco has confirmed that a cybercriminal successfully carried out a voice phishing (vishing) attack that [...]
Aug
Remote Code Execution Risk Found in Cursor AI Editor — Vulnerability Highlights AI Supply Chain Threats
Security researchers have uncovered a high-severity vulnerability in the AI-powered code editor Cursor, potentially enabling [...]
Aug
Google Fixes Critical Android Flaws — Update Your Device Now
Google has released its August 2025 Android Security Bulletin, which includes patches for six vulnerabilities, [...]
Aug
$1 Million Up for Grabs: Pwn2Own Challenges Hackers to Break WhatsApp Without a Click
Security researchers will soon gather in Cork, Ireland, for one of the most anticipated cybersecurity [...]
Aug
Google’s AI-Powered Vulnerability Hunter Makes Its Debut with 20 Reported Security Flaws
In a major milestone for artificial intelligence in cybersecurity, Google has announced that its AI-based [...]
Aug
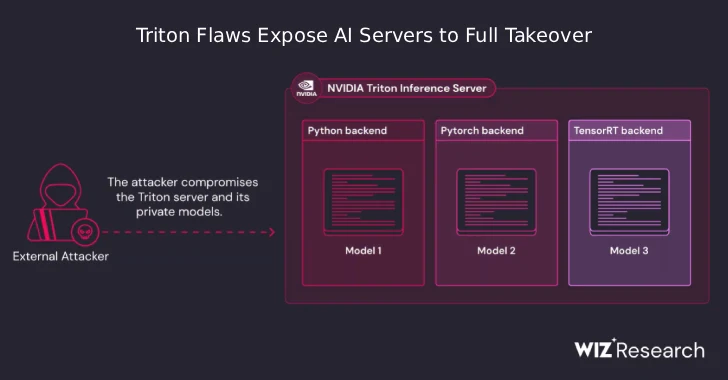
Critical NVIDIA Triton Server Vulnerabilities Could Let Hackers Hijack AI Infrastructure
A series of newly identified security flaws in NVIDIA’s open-source Triton Inference Server for Windows [...]
Aug
AI Web Usage Surge Reshapes Global Internet Traffic Trends
The rapid adoption of AI technologies is significantly reshaping global internet traffic patterns. A recent [...]
Aug
Massive Data Breach at Northwest Radiologists Affects Over 350,000 Residents
Northwest Radiologists, a medical imaging provider based in Bellingham, Washington, has confirmed a major data [...]
Aug
OpenAI Disables “Discoverable Chats” Feature in ChatGPT
OpenAI has quietly discontinued an experimental option in ChatGPT that let users make their conversations [...]
Aug
Threat Actors Exploit Fake OAuth Apps with Tycoon Kit to Compromise Microsoft 365 Accounts
A newly identified cyberattack campaign is raising serious concerns among security professionals. Threat actors are [...]
Aug
Google Chrome Introduces Store Reviews to Help Users Spot Legit Retailers
Online shopping just got a little safer, thanks to a new feature in Google Chrome [...]
Aug
Hackers Target Vulnerabilities Weeks Before Public Disclosure, Report Warns
A recent study from GreyNoise reveals a concerning trend in cyberattacks: threat actors are actively [...]
Aug
Russian APT Secret Blizzard Uses ISP-Level AitM Attacks to Target Foreign Embassies in Moscow
Microsoft has uncovered a cyberespionage campaign carried out by the Russian state-backed group Secret Blizzard, [...]
Aug
Minnesota Deploys National Guard Cyber Experts Following Cyberattack on Saint Paul
On July 30, 2025, Minnesota Governor Tim Walz activated the National Guard’s cybersecurity specialists to [...]
Jul
FunkSec Ransomware Victims Can Now Recover Encrypted Files for Free
In a major win for cybersecurity efforts, researchers at Avast have released a free decryptor [...]
Jul
DoubleTrouble: Sophisticated Android Banking Malware Now Spreads via Discord
A powerful Android banking Trojan known as DoubleTrouble has recently evolved, expanding both its attack [...]
Jul
New Multi-Layer Redirect Tactic Targets Microsoft 365 Credentials
Cybersecurity researchers have uncovered a new phishing method that uses multi-layer URL redirects to steal [...]
Jul
That Random Text Message Might Be a Scam – Here’s Why You Shouldn’t Reply
Most of us have received those strange, unexpected text messages. They often seem harmless: a [...]
Jul
Apple Releases Urgent iOS and iPadOS Security Updates to Fix 29 Vulnerabilities
Apple has issued critical security updates for iOS and iPadOS, addressing nearly 30 vulnerabilities — [...]
Jul
JSCEAL Malware Spread via Facebook Ads and Fake Crypto Trading Apps
A new and sophisticated cyber campaign is exploiting Facebook ads to distribute fake cryptocurrency trading [...]
Jul
Critical Flaws in Dahua Cameras Enable Remote Takeover Through ONVIF and File Upload Exploits
Security researchers have uncovered two critical vulnerabilities in the firmware of popular Dahua smart cameras, [...]
Jul
Raspberry Pi Used to Breach ATM Network and Deploy Hidden Backdoor
A sophisticated cyberattack has been uncovered involving the use of a Raspberry Pi to infiltrate [...]
Jul
Nearly 400 Microsoft SharePoint Systems Compromised Globally in Targeted Cyber Campaign
A major wave of cyberattacks has compromised at least 396 Microsoft SharePoint servers worldwide, exploiting [...]
Jul
Pro-Ukraine Hackers Disrupt Aeroflot Operations in Major Cyberattack
A significant cyberattack attributed to pro-Ukrainian hacktivist groups forced Russia’s largest airline, Aeroflot, to cancel [...]
Jul
Lenovo Firmware Flaws Open the Door to Persistent System Implants
New security research by Binarly has revealed multiple critical firmware vulnerabilities in Lenovo devices, highlighting [...]
Jul
Orange Confirms Cyber Attack Disrupting Services in France
Orange, the leading telecommunications provider in France, has confirmed that it was the target of [...]
Jul
Second Data Breach at Tea App Exposes Over 1.1 Million Private Messages
The dating safety app Tea, known for its mission to provide a safe space for [...]
Jul
Ongoing Phishing Campaign Targets PyPI Users with Fake Verification Emails
The Python Package Index (PyPI) has issued a security advisory warning developers about an active [...]
Jul
NASCAR Discloses Data Breach Following Ransomware Incident in April 2025
The National Association for Stock Car Auto Racing (NASCAR) has confirmed that a ransomware attack [...]
Jul
Naval Group Refutes Data Breach Allegations Amid Suspected Reputation Attack
Naval Group, a major French defense contractor partially owned by the French government, has firmly [...]
Jul
Cyberattack Grounds Aeroflot Flights as Hackers Claim Destruction of Core Systems
A significant cyberattack has disrupted air travel across Russia after Aeroflot, the nation’s largest airline, [...]
Jul
Data Breach at Women-Centered Dating App Exposes Thousands of User Photos
A recent cybersecurity incident has impacted Tea, a dating app designed to prioritize women’s safety, [...]
Jul
Scattered Spider Targets VMware ESXi in Advanced Ransomware Attacks on U.S. Critical Infrastructure
The threat group known as Scattered Spider has launched a new wave of cyberattacks focusing [...]
Jul
Chaos Ransomware: A New Threat Actor Launches Sophisticated Global Attacks
A newly emerged ransomware group, known as Chaos, has initiated a series of widespread cyberattacks [...]
Jul
Targeted Cyber Espionage Campaign Strikes Russian Aerospace with EAGLET Backdoor
A recent cyber espionage operation, identified as Operation CargoTalon, has taken aim at Russia’s aerospace [...]
Jul
AI-Powered Koske Malware: A New Era of Adaptive Linux Threats
A recent report by Aqua Security sheds light on Koske, an advanced Linux-based malware that [...]
Jul
BlackSuit Ransomware Sites Taken Down in Global Police Operation ‘Checkmate’
The notorious ransomware group BlackSuit has suffered a major blow after its dark web infrastructure [...]
Jul
UK Student Jailed for Distributing Phishing Kits That Caused $134M in Losses
In a significant blow against cybercrime, a 21-year-old UK resident has been sentenced to seven [...]
Jul
iPhone vs. Android: Who’s Really Safer Online? Malwarebytes Report Reveals Surprising Results
The never-ending debate between iPhone and Android users has taken a new twist—this time, it’s [...]
Jul
CastleLoader: A New Stealthy Malware Loader Targeting Developers and Users via GitHub and Phishing
A newly identified malware loader named CastleLoader is rapidly becoming a favorite tool among cybercriminals, [...]
Jul
UK to Enforce Age Verification Law Starting July 25: What You Need to Know
Beginning July 25, 2025, the United Kingdom will implement a new age-verification law that requires [...]
Jul
SarangTrap: A Sophisticated Malware Campaign Disguised as Dating Apps
A newly discovered large-scale malware campaign, identified as SarangTrap, is targeting mobile users by posing [...]
Jul
New York Seeks Public Input on Proposed Cybersecurity Rules for Water Systems
In a significant move to strengthen critical infrastructure, the State of New York has released [...]
Jul
New Coyote Malware Variant Exploits Windows UI Automation to Steal Banking Credentials
A new variant of the Windows banking trojan known as Coyote has been identified as [...]
Jul
Google Unveils OSS Rebuild to Strengthen Open-Source Software Security
Google has launched a new initiative, OSS Rebuild, designed to enhance the security of open-source [...]
Jul
France Travail Data Breach Exposes Personal Information of 340,000 Jobseekers
France Travail, the French national employment agency, discovered a cybersecurity breach affecting its employment portal [...]
Jul
AI Voice Cloning Sparks Growing Concerns in Banking Sector, Warns OpenAI CEO
Artificial intelligence has reached a point where it can convincingly mimic human voices—so convincingly, in [...]
Jul
AT&T Introduces Wireless Account Lock to Combat SIM Swapping Threats
AT&T has launched a new feature aimed at helping customers protect themselves from SIM swapping [...]
Jul
Credential Theft on the Rise: Mexican Organizations Targeted by AllaKore, PureRAT, and Hijack Loader Campaigns
In recent months, there has been a noticeable surge in credential theft and remote access [...]
Jul
UK Government Proposes Mandatory Ransomware Reporting to Disrupt Threat Actors
In a bold move to combat cybercrime, the UK government has unveiled a new proposal [...]
Jul
Cybercriminals Leverage AI Chatbot to Automate Ransomware Negotiations
In a concerning evolution of ransomware tactics, a newly rebranded ransomware-as-a-service (RaaS) operation known as [...]
Jul
Dell Responds to Alleged Data Leak: Claims Leaked Files Are Not Real
Dell Technologies has confirmed that one of its environments was accessed by threat actors, but [...]
Jul
Helmholz REX 100 Industrial Routers Found Vulnerable to Remote Attacks: Critical Flaws Patched
A new wave of industrial cybersecurity concerns has emerged following the discovery of eight security [...]
Jul
Ring Camera “Hack” Claims Spark Concerns — But Amazon Blames a Backend Bug
In recent days, numerous Amazon Ring users have taken to platforms like TikTok, Reddit, and [...]
Jul
Phishing Attack Compromises Maintainer Credentials, Injects Malware into Popular npm Packages
A recent software supply chain attack has raised alarms in the cybersecurity community, after threat [...]
Jul
New Zero-Day Vulnerability in Microsoft SharePoint Actively Exploited in Widespread Attacks
A critical vulnerability recently discovered in Microsoft SharePoint is being actively exploited, prompting urgent alerts [...]
Jul
Malware Campaign Targets US Accounting Firm Using New Crypter “Ghost Crypt”
In May 2025, a sophisticated malware campaign targeted a U.S.-based accounting firm, delivering the PureRAT [...]
Jul
Iranian APT MuddyWater Deploys New Versions of DCHSpy Android Spyware Amid Israel Conflict
The ongoing geopolitical tension between Iran and Israel has sparked a new wave of cyber [...]
Jul
Hackers Exploit Critical Flaw in Signal Clone TeleMessage to Target Sensitive Data
Cybersecurity researchers and U.S. government officials are raising alarms over a growing wave of attacks [...]
Jul
LameHug: New AI-Powered Malware Targets Ukrainian Defense Sector
A newly discovered malware strain named LameHug is using artificial intelligence to dynamically generate malicious [...]
Jul
Retail Takes the Spotlight as Ransomware Threats Shift Away from Healthcare
While ransomware attacks are increasing across most industries, a new analysis by Comparitech reveals that [...]
Jul
Over 1.4 Million Impacted in Data Breach at Virginia Radiology Provider
Radiology Associates of Richmond (RAR), a medical imaging services provider based in Virginia, has confirmed [...]
Jul
Weak Passwords and Malware Lead to Security Breach at AI Hiring Platform Paradox.ai
Security concerns have once again come to light in the AI recruitment industry. Paradox.ai, a [...]
Jul
Ransomware Gang DragonForce Claims Responsibility for Cyberattack on Belk
The US department store chain Belk has become the latest high-profile target of a ransomware [...]
Jul
MITRE Introduces New Cybersecurity Framework to Mitigate Cryptocurrency Risks
The renowned cybersecurity organization MITRE has unveiled a new framework designed to tackle the growing [...]
Jul
Episource Data Breach Affects Over 5 Million Americans: A Stark Reminder of Cybersecurity Gaps in Healthcare
Episource, a major player in the U.S. healthcare billing ecosystem, is in the spotlight after [...]
Jul
Major News Sites Impersonated in Global Investment Scam Campaign
Cybersecurity researchers have uncovered a massive scam campaign in which fake websites impersonate reputable media [...]
Jul
Google Breaks 10-Year Streak of Monthly Android Security Patches
In an unexpected turn of events, Google has not issued any Android security patches in [...]
Jul
Malicious Chrome and Edge Extensions Spied on Millions of Users
Security researchers recently uncovered a major privacy breach involving 18 browser extensions for Google Chrome [...]
Jul
Millions of Vehicles at Risk from New Bluetooth Vulnerabilities Known as “PerfektBlue”
Cybersecurity researchers have uncovered a critical set of Bluetooth vulnerabilities affecting millions of vehicles across [...]
Jul
Weak Password on AI Hiring Bot Exposed Data of 64 Million McDonald’s Job Applicants
A significant security lapse was recently uncovered in an AI-powered recruitment tool used by McDonald’s, [...]
Jul
NCSC Advises Urgent Migration to Windows 11 to Prevent Cybersecurity Risks
The UK’s National Cyber Security Centre (NCSC) has issued a strong recommendation for organizations still [...]
Jul
Google Gemini Vulnerability Exposes Users to Hidden Phishing Attacks
A newly discovered vulnerability in Google Gemini for Workspace has raised concerns about AI-driven email [...]
Jul
Samsung Urges Galaxy Users to Activate New Anti-Theft Features
Samsung is advising all Galaxy phone users to enable its latest anti-theft protections—part of a [...]
Jul
Hackers Force Activision to Pull Call of Duty: WWII PC Version Due to Security Flaw
Activision has temporarily taken down the Microsoft Store version of Call of Duty: WWII after [...]
Jul
Qantas Faces Extortion Attempt Following Major Data Breach
Australian airline Qantas has confirmed that it is the target of an extortion attempt following [...]
Jul
RedDirection: 18 Malicious Chrome and Edge Extensions Still Active and Spying on Users
Security researchers from Koi Security have uncovered a coordinated malware campaign involving 18 browser extensions [...]
Jul
Google Expands Gemini AI Access to Your Android Apps—Privacy Questions Arise
If you’re an Android user, now is a good time to double-check your privacy settings. [...]
Jul
Like Ransoming a Bike: How Organizational Muscle Memory Drives Effective Ransomware Response
Ransomware continues to pose a significant threat to enterprises, with a 37% increase reported in [...]
Jul
Undetectable Android Spyware Catwatchful Exposes Over 62,000 User Credentials
A serious security flaw in Catwatchful, an Android spyware disguised as parental control software, has [...]
Jul
Hacked, Leaked, and Exposed: The Critical Risks of Using Stalkerware Applications
In today’s digital landscape, there exists a troubling segment of software known as stalkerware—applications designed [...]
Jul
Facebook’s New AI Feature Requests Photo Uploads for Story Suggestions, Raising Privacy Concerns
Meta-owned Facebook has introduced a new AI-powered feature that prompts users to upload photos from [...]
Jul
New Dangerous Malware Targets Photos on Android and iOS Devices, Raising Crypto Security Concerns
Cybersecurity experts at Kaspersky have identified a new sophisticated malware strain called SparkKitty, which has [...]
Jul
Airoha Chip Vulnerabilities Put Headphones at Risk of Takeover Attacks
Security researchers have identified multiple critical vulnerabilities in Bluetooth system-on-chip (SoC) products developed by Airoha, [...]
Jul
Hawaiian Airlines Reports Cybersecurity Incident Affecting IT Systems
Hawaiian Airlines has confirmed it experienced a cybersecurity incident that disrupted portions of its IT [...]
Jun
Nearly Half of Online Signups Now Fraudulent, Warns Okta
In a stark warning to organizations worldwide, identity and access management provider Okta has revealed [...]
Jun
Microsoft Introduces Free and Paid Options for Windows 10 Security Updates Ahead of 2025 End of Support
As Windows 10 approaches its official end of support (EOS) on October 14, 2025, Microsoft [...]
Jun
Rogue WordPress Plugin Campaign Targets Online Stores with Skimming and Credential Theft
Cybersecurity researchers have uncovered a sophisticated malware campaign targeting WordPress websites through a fake plugin [...]
Jun
Echo Chamber: The Sophisticated Jailbreak Method Exploiting AI Language Models
Cybersecurity researchers are warning about a new and dangerously effective technique to bypass the safety [...]
Jun
XDigo Malware Exploits Windows LNK Vulnerability in Targeted Attacks Across Eastern Europe
Cybersecurity analysts have identified a new strain of Go-based malware, named XDigo, actively used in [...]
Jun
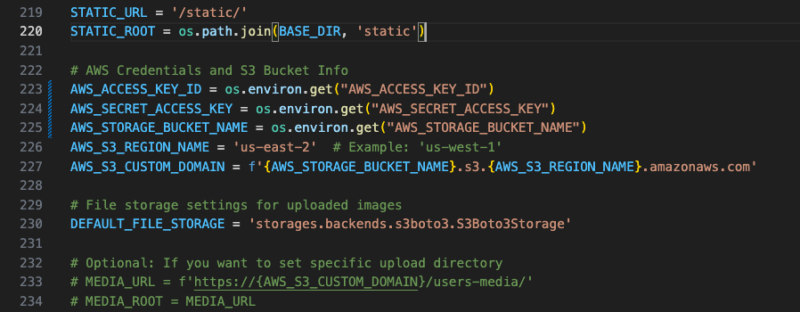
How to Securely Connect Django to AWS S3 — Two Recommended Approaches — Secure Setup Guide
When deploying Django apps on AWS, securely managing your access to S3 is critical. Hardcoding [...]
Jun
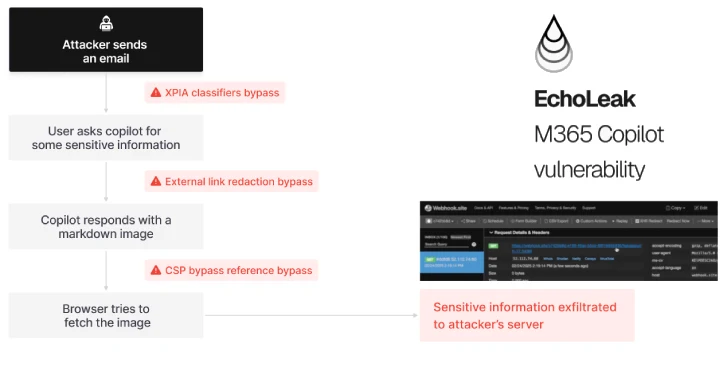
EchoLeak: Critical Zero-Click Vulnerability in Microsoft 365 Copilot Exposes Sensitive Data Without User Interaction
A newly discovered threat called EchoLeak has been classified as a zero-click vulnerability affecting Microsoft [...]
Jun
Meta and Oakley Launch New Smart Glasses Designed for Performance and Style
After months of speculation, Meta has officially revealed its latest wearable tech: a new line [...]
Jun
AI Becomes a Key Player in Spam and Scam Email Campaigns
More than half of today’s spam and malicious emails are now being generated by artificial [...]
Jun
Hydra WordPress Brute Force Attack
In this tutorial, I will explain in detail how to perform a brute force attack [...]
May
What is Phishing?
Phishing, as its name suggests, is literally information fishing. When we talk about a cyber [...]
May
What is Ngrok and How to Install It?
Ngrok is a service or tool that allows you to turn your local server into [...]
May
What is Setoolkit?
Setoolkit or SET is an open-source framework for performing pentesting focused on Social Engineering attacks. [...]
May
Ngrok + Setoolkit Kali Linux 2020 – Phishing Attack
In this tutorial, I’m going to explain how to do phishing. But before that, I [...]
May
How to Install Kali Linux on Mac 2020
First of all, we need to make sure that Virtual Box for Mac is installed, [...]
May
How to Install VirtualBox 2020
Go to the official Virtual Box website: https://www.virtualbox.org/wiki/Downloads Download the one for your OS where [...]
May
What is the Difference Between a Synchronous and Asynchronous Action in React Redux?
Summarizing the answer as much as possible, an asynchronous action has a callback and the [...]
May
How Do I Take a Piece of My Status to Print It Somewhere?
useSelector is used to obtain information from the state. const state = useSelector(state => state); [...]
May
What is Live Streaming Shopping?
It is common to find product demonstration videos created by third parties; however, it sounds [...]
May
Achieve Your Goals with Habits
Achieve all your goals with Habits. A true gem. A FREE app available for IOS [...]
May
Change Your Router Password
If I had to give you only one cybersecurity tip, it would definitely be this: [...]
May
Songs Created Virtually with AI
Did you know these songs were virtually created with AI? Without a doubt, AI has [...]
May
Get to Know the Pebble Flow
Can you imagine going on a picnic in a fully electric RV with a futuristic [...]
May
Honda Series 0: A Futuristic Car
Are you ready to have a futuristic car? Well, let me tell you that Honda [...]
May
Today Marks 40 Years Since the First Macintosh
Today, January 24th, marks 40 years since the first Macintosh was released to the market. [...]
May
Buick Riviera: First Touchscreen in a Car
Did you know that the first touchscreen in a car was created in 1986? That’s [...]
May
Goodbye Dodge Challenger
The last Dodge Challenger has rolled off the plant where it was manufactured. And this [...]
May
Universal Leaves TikTok
Universal leaves TikTok, what is the real reason? We all heard the news that Universal [...]
May
What is the Holo Tile Floor?
Disney brings you the perfect complement for your virtual reality games. The Holo Tile Floor [...]
May
Virtual Influencers: Did You Know They Exist?
What if I told you that your favorite influencer does NOT exist? Virtual influencers are [...]
May
Coffee Shops with AI
What if you could leverage your surveillance cameras to see data like time and productivity, [...]
May
Change the Color of Your Eyes?
Change the color of your eyes? Would you be willing to undergo surgery to do [...]
May
How to Fix the ‘502 Bad Gateway’ Error in Django Deployed on AWS Elastic Beanstalk
Introduction The “502 Bad Gateway” error is common when Nginx, acting as a reverse proxy, [...]
May
Setting Up a React Frontend on Amazon S3 and CloudFront
This tutorial will guide you through the steps to set up your React frontend on [...]
May
Tutorial #1: Create a Local Variable on Your System
For macOS or Linux: Step 1: Open the Terminal. Step 2: Determine which shell you [...]
May
Setting Up an Environment Variable in AWS Elastic Beanstalk
Step 1: Access Elastic Beanstalk Log in to your AWS console and navigate to Elastic [...]
May
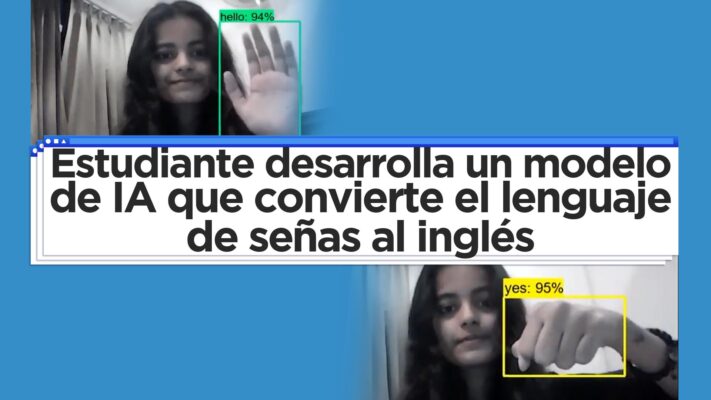
Sign Language Translator
The sign language translator created by Priyanjali Gupta — How was it made? She is [...]
May
Chess Master
Tunde Onakoya, the chess master, recently surprised everyone. When? At a Chess exhibition held in [...]
May
BMW CEO Fires Mercedes Benz
And this is how BMW says goodbye to the Mercedes Benz CEO. In 2019, Dieter [...]
May
Do You Read a Lot on the Internet?
If you read a lot on the internet, in this blog I’m going to give [...]
May
Gadgets & Software That Made Me More Productive
Tech Gadgets and Software That Made Me MUCH More Productive (Part 1) In 2022, I [...]
May
Digital Decade
This is how the EU achieved humanity’s first AI regulation through the “Digital Decade” initiative. [...]
May
Using NameDrop to Share Your Contact
Do you know the newest and ultimate way to share your contact if you have [...]
May
BenQ Monitor – Gadgets and Software (Part 2)
Another tech purchase that was definitely beneficial for me in 2023 was the BenQ monitor [...]
May
Planning to Hire Someone for Your Website? Here’s the Most Valuable Tip
This is the MOST valuable TIP you’ll hear when you’re about to hire your website [...]
May
Why Do E-commerce Sites Hate Google?
In this video, I’m going to tell you what the BIG e-commerce companies around the [...]
May
How to Share Your Wi-Fi Quickly and Securely?
We’ve noticed that many people still share Wi-Fi passwords by saying them out loud or [...]
May
Was Your iPhone Stolen or Did You Lose It?
Almost everyone has gone through this, or might go through it eventually — it’s almost [...]
May
How Do Computers Communicate?
It is very important to understand this concept of how computers communicate because in cyberattacks [...]
May
Industries We Serve
We provide flexible technology solutions tailored to the realities of different sectors. Our clients range from tech-driven startups to established mid-sized organizations in:
Retail & Hospitality
Manufacturing & Logistics
Professional Services
Agribusiness & Natural Resources
Healthcare & Education
The right expert for every challenge
Each client has unique needs. That’s why we tailor our delivery and team structure to fit your context — from onboarding to ongoing support. Whether it’s software, security or observability, Nubetia brings the right skills to the table.
TESTIMONIALS
Fernando de la mano de Nubetia es nuestro proveedor de ciberseguridad , nos apoyo en la cuestión de implementación , soporte de ThreatDown by Malwarebytes , junto con esto tambien nos ha impartido una capacitación para familiarizarnos con este nuevo sistema como Ingeniero de IT y Cliente , estamos contentos con el servicio proporcionado el poder trabajar mano a mano con el ha sido genial y de gran ayuda en cada cuestión , tener la seguridad , certeza y apoyo por parte de Fernando y Nubetia , genera confianza , y nos permite trabajar dia a dia sin preocuparnos por temas de ciberseguridad , sin duda recomiendo el servicio .
Jesus
Tamaulipas
We’ve been with Nubetia for almost 10 years. Always reliable and ahead of the curve.
Monica
San Antonio – Texas
Highly motivated and skilled team. Great and professional service.
Gabriel
Mexico City – Mexico
They find solutions fast and are transparent with what they can deliver. Great collaboration.
Roberto
Monterrey – Mexico
Your next tech partner is nearshore, and ready.
Let’s build scalable, secure, and compliant systems together. Reach out to our team — we’re ready to listen and act.
Our Nearshore Service Packages
Tailored by company size, IT maturity, and business need.
Must
Ideal for small teams (25–50 employees) looking to protect and modernize with essential services.
- Malwarebytes EDR
- Monthly reports
- Basic observability
- Cloud backups & IAM
- More…
Starting as low
$8,990 / month
Growth
For mid-sized orgs (50–100 employees) that need deeper visibility and stronger defense.
- Incident response
- Hardening & Gmail security
- Custom dashboards
- Multi-environment AWS
- More…
$32,000 / month
Enterprise
For complex operations (100–150 employees) requiring full-stack services & compliance support.
- SIEM integration
- Compliance audits (NOM-151)
- 24/7 support & alerting
- Executive observability reports
- More…
$70,000–$85,000 / month
Start working with us
Let’s have coffee and talk business. Reach us anytime via email or set up a discovery call.
Send e-mailWant to chat first?
Chat with us on WhatsApp. We’re available Monday–Friday from 9am to 6pm (CST).
Chat on WhatsApp
 Español
Español