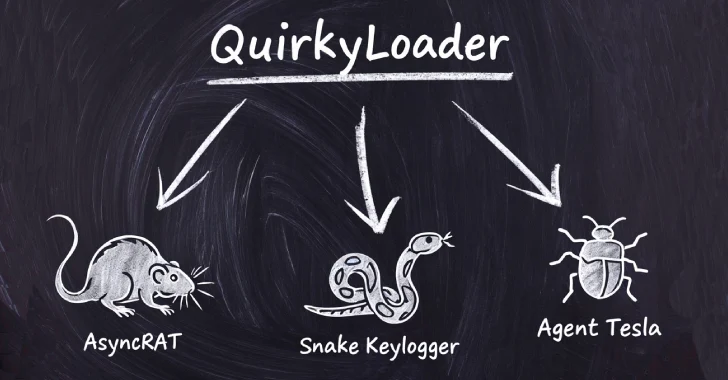
Hackers Exploit New QuirkyLoader Malware to Deploy Agent Tesla, AsyncRAT, and Snake Keylogger
ybersecurity experts have recently uncovered a new malware loader, dubbed QuirkyLoader, that has been actively [...]
Aug
Password Managers Exposed to Clickjacking Threats: Research Reveals Vulnerabilities
A recent study has uncovered that many popular password managers are at risk of clickjacking [...]
Aug
Colt Confirms Possible Customer Data Breach After Cyber Attack
Colt Technology Services has acknowledged that sensitive customer data may have been accessed and is [...]
Aug
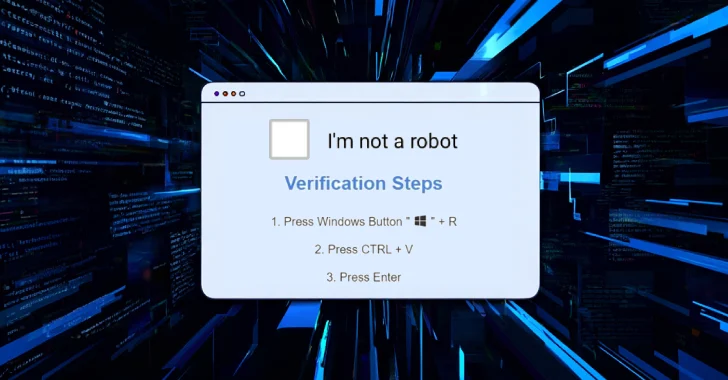
Cybercriminals Exploit ClickFix Tactic and Fake CAPTCHA Pages to Deploy CORNFLAKE.V3 Backdoor
Cybercriminals continue to refine their social engineering tactics, with recent campaigns leveraging fake CAPTCHA pages [...]
Aug
Google Reaches $30 Million Settlement in YouTube Child Privacy Case
August 21, 2025 – Google has agreed to a $30 million settlement in the United [...]
Aug
GPT-5 Faces Vulnerability: Router Can Redirect Queries to Older, Less Secure Models
A newly discovered vulnerability in GPT-5 could redirect user queries from the advanced GPT-5 Pro [...]
Aug
Inotiv Confirms Ransomware Attack Affecting Key Systems and Data
Inotiv, a pharmaceutical research company based in Indiana, has confirmed that it suffered a ransomware [...]
Aug
UAE-Based Startup Offers Up to $20 Million for Zero-Day Exploits Targeting Smartphones
A new cybersecurity startup based in the United Arab Emirates, Advanced Security Solutions, has entered [...]
Aug
PromptFix Exploit: How AI Browsers Are Being Tricked into Hidden Malicious Actions
Cybersecurity researchers have uncovered a novel attack method known as PromptFix, a prompt injection exploit [...]
Aug
Mule Operators in META Region Evolve Into Complex Fraud Networks
Fraud activity across the Middle East, Turkey, and Africa (META) is entering a new phase [...]
Aug

 Español
Español