In this tutorial, I will explain in detail how to perform a brute force attack on a WordPress site. We will use the popular and powerful tool Hydra, which comes pre-installed on Kali Linux, and if you don’t have Kali Linux, you can download it for your operating system. Hydra is a pentesting program that […]
Category Archives: Cybersecurity
Phishing, as its name suggests, is literally information fishing. When we talk about a cyber attack of the phishing type, it is when a hacker creates a copy or clones a website to send it to their potential victims and try to “fish” or capture the data that their victims enter on the cloned site […]
Ngrok is a service or tool that allows you to turn your local server into a server accessible via a subdomain randomly generated by ngrok, enabling you to view it from any computer with internet access worldwide. This is very useful to show progress to your clients on a website, or similarly, malicious hackers use […]
Setoolkit or SET is an open-source framework for performing pentesting focused on Social Engineering attacks. Social engineering is the art of obtaining information from users through manipulating people. Therefore, in every security audit of companies, it is extremely important to audit the weakest point in cybersecurity within companies: the employees. The company Trusted Sec developed […]
In this tutorial, I’m going to explain how to do phishing. But before that, I will explain the following: What is Phishing in cybersecurity?: https://www.nubetia.com/que-es-phishing/ What is Ngrok and how to install it?: https://www.nubetia.com/que-es-ngrok/ What is Setoolkit?: https://www.nubetia.com/que-es-setoolkit/ Now that we know what phishing, ngrok, and setoolkit are, we will proceed to perform a phishing attack on […]
First of all, we need to make sure that Virtual Box for Mac is installed, which you can download at the following link: https://www.virtualbox.org/wiki/Downloads Go to the following link: https://www.offensive-security.com/kali-linux-vm-vmware-virtualbox-image-download/#1572305786534-030ce714-cc3b Download Kali Linux for Virtual Box; I select the 64-bit version because that corresponds to my machine. Once downloaded, open the file and click on […]
If I had to give you only one cybersecurity tip, it would definitely be this: Change your router password. You need “ZERO” technical knowledge. That means anyone can do it, from kids to seniors. And it will be a great shield to protect you from internet threats. Including theft of banking information, personal data, and […]
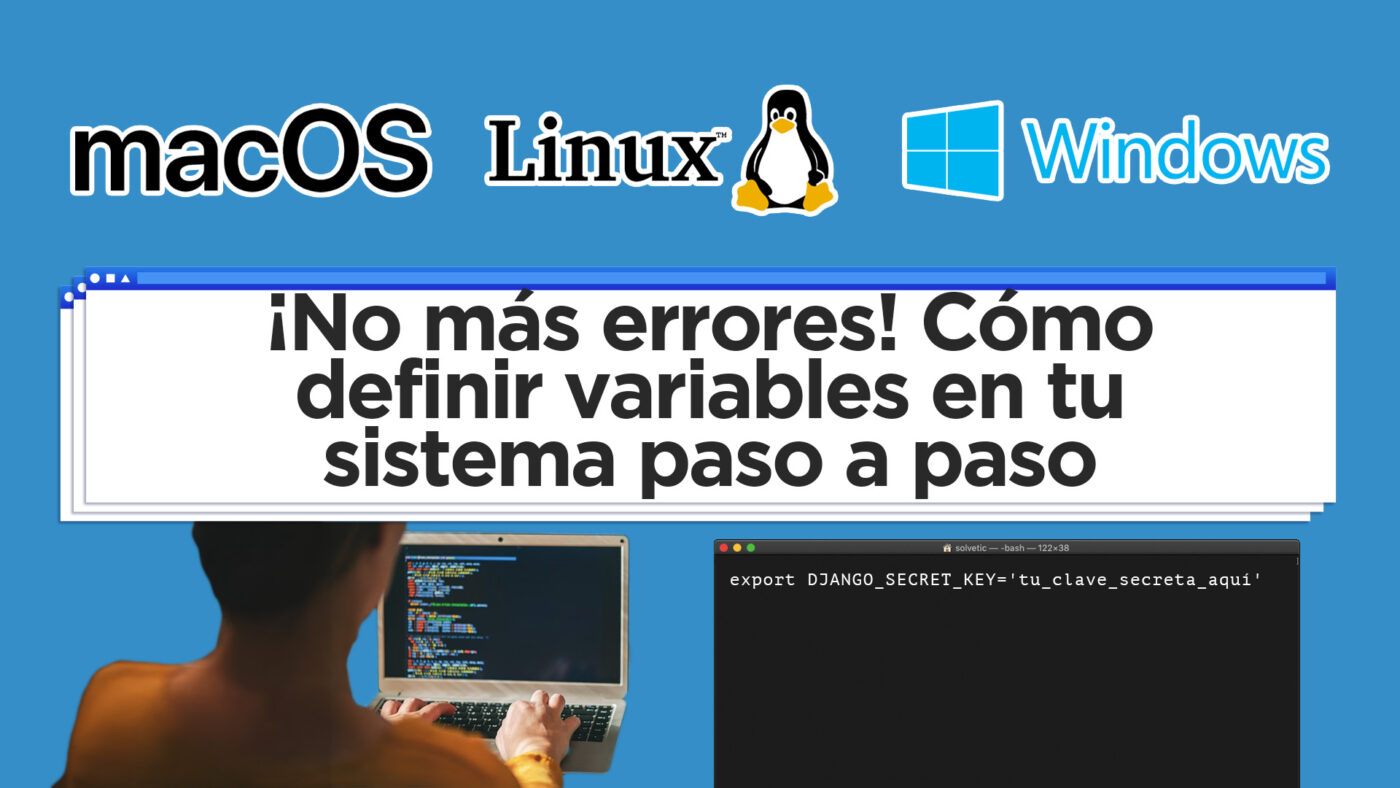
For macOS or Linux: Step 1: Open the Terminal. Step 2: Determine which shell you are using. Generally, macOS and many Linux distributions use bash or zsh. You can find out with the command: Step 3: Based on the shell you use, choose one of the following files to edit: .bashrc for Bash or .zshrc […]
Step 1: Access Elastic Beanstalk Log in to your AWS console and navigate to Elastic Beanstalk. Select your application. Step 2: Select Your Environment Choose the specific environment of your application where you want to add the environment variable. Step 3: Environment Configuration On the environment summary page, locate the “Configuration” section. Step 4: Modify […]
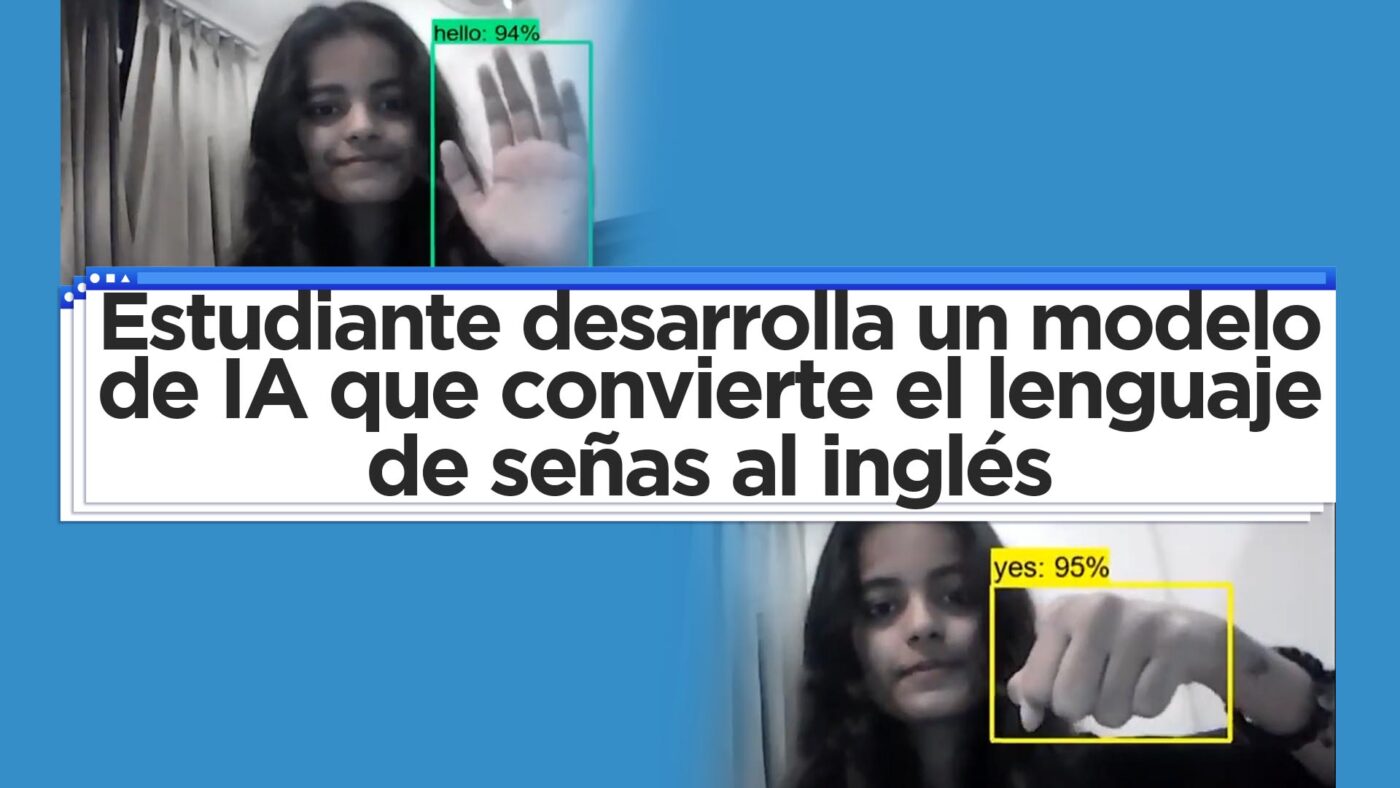
The sign language translator created by Priyanjali Gupta — How was it made? She is a third-year Engineering student at Vellore Institute of Technology in India. She developed a model that uses artificial intelligence to instantly convert sign language into English words. Previously, in 2020 and 2021, Nicholas Renotte uploaded tutorials to his YouTube channel […]

 Español
Español