The operators behind the Noodlophile malware have broadened their global activities, using spear-phishing emails and refined delivery techniques to target enterprises across the U.S., Europe, the Baltics, and the Asia-Pacific (APAC) region.
According to a recent report by Morphisec researcher Shmuel Uzan, the campaign—which has been active for more than a year—now uses sophisticated phishing messages disguised as copyright violation notices. These emails are customized with reconnaissance-based details such as Facebook Page IDs and company ownership information to make them appear legitimate.
Back in May 2025, Morphisec first detailed Noodlophile’s use of fake AI-powered tools promoted through social media platforms like Facebook as lures to spread the malware. The latest campaign, however, marks an escalation, relying heavily on legitimate software vulnerabilities, Telegram-based obfuscation, and dynamic payload execution.
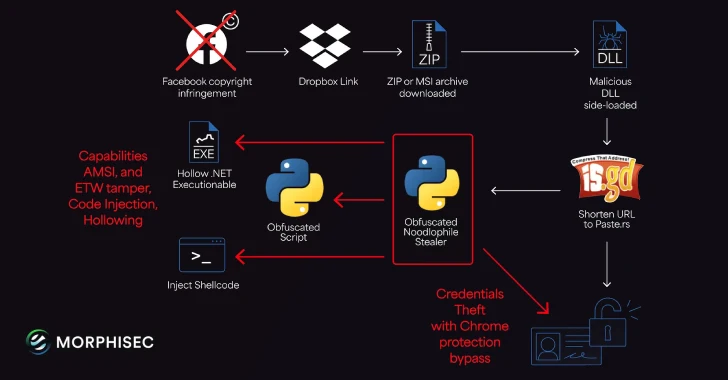
The attack chain begins with a phishing email sent from Gmail accounts to avoid suspicion. These messages claim alleged copyright violations on specific Facebook Pages to pressure employees into urgent action. Inside the email, a Dropbox link delivers a ZIP or MSI installer, which sideloads a malicious DLL via Haihaisoft PDF Reader binaries. Before the final Noodlophile payload is deployed, batch scripts are executed to establish persistence through the Windows Registry.
What makes this campaign particularly evasive is the use of Telegram group descriptions as a “dead drop resolver” to point victims to the real server (paste[.]rs) hosting the payload. This technique, combined with Base64-encoded archives, LOLBin tools like certutil.exe, and in-memory execution, significantly complicates detection and takedown efforts.
Once installed, Noodlophile functions as a fully equipped information stealer. It extracts data from web browsers, collects system details, and—based on its source code—is under active development to include capabilities such as screenshot capture, keylogging, file exfiltration, process monitoring, network reconnaissance, file encryption, and browser history harvesting.
Morphisec highlights that the heavy focus on browser data theft reflects a clear intent to compromise enterprises with large social media footprints, especially on platforms like Facebook. The ongoing development of unimplemented features suggests that Noodlophile could evolve into an even more versatile and dangerous threat in the near future.
Source: https://thehackernews.com/2025/08/noodlophile-malware-campaign-expands.html

 Español
Español