Cybersecurity
Akira Ransomware Continues Exploiting SonicWall Vulnerability Using Legitimate Tools
Security researchers warn that the Akira ransomware group is still actively exploiting a year-old SonicWall [...]
Sep
Microsoft Thwarts AI-Generated Phishing Campaign Targeting US Organizations
Microsoft Threat Intelligence recently intercepted a sophisticated phishing campaign that appears to have leveraged AI-generated [...]
Sep
How AI is Transforming Cyberattacks According to Wiz CTO Ami Luttwak
Ami Luttwak, chief technologist at cybersecurity firm Wiz, recently shared insights with TechCrunch on how [...]
Sep
First Malicious MCP Server Exposed in Rogue Postmark-MCP Package
Cybersecurity researchers have identified the first-ever case of a malicious Model Context Protocol (MCP) server [...]
Sep
Amazon Agrees to $2.5 Billion Settlement Over Prime Practices
Amazon has agreed to a $2.5 billion settlement with the Federal Trade Commission (FTC) following [...]
Sep
Cognex Industrial Camera Vulnerabilities Pose Risks Without Available Patches
Several industrial cameras produced by Cognex have been identified with serious security vulnerabilities, and the [...]
Sep
Jaguar Land Rover Initiates Phased Recovery Following Cyber-Attack
Jaguar Land Rover (JLR) has started a gradual restart of its operations after a significant [...]
Sep
Massive Exposure of Indian Bank Transfer Records After Cloud Security Misconfiguration
A recent data exposure incident has raised alarms in India’s financial sector, after hundreds of [...]
Sep
Software
What is the Difference Between a Synchronous and Asynchronous Action in React Redux?
Summarizing the answer as much as possible, an asynchronous action has a callback and the [...]
May
How Do I Take a Piece of My Status to Print It Somewhere?
useSelector is used to obtain information from the state. const state = useSelector(state => state); [...]
May
Achieve Your Goals with Habits
Achieve all your goals with Habits. A true gem. A FREE app available for IOS [...]
May
Virtual Influencers: Did You Know They Exist?
What if I told you that your favorite influencer does NOT exist? Virtual influencers are [...]
May
Change the Color of Your Eyes?
Change the color of your eyes? Would you be willing to undergo surgery to do [...]
May
How to Fix the ‘502 Bad Gateway’ Error in Django Deployed on AWS Elastic Beanstalk
Introduction The “502 Bad Gateway” error is common when Nginx, acting as a reverse proxy, [...]
May
Setting Up a React Frontend on Amazon S3 and CloudFront
This tutorial will guide you through the steps to set up your React frontend on [...]
May
DevOps
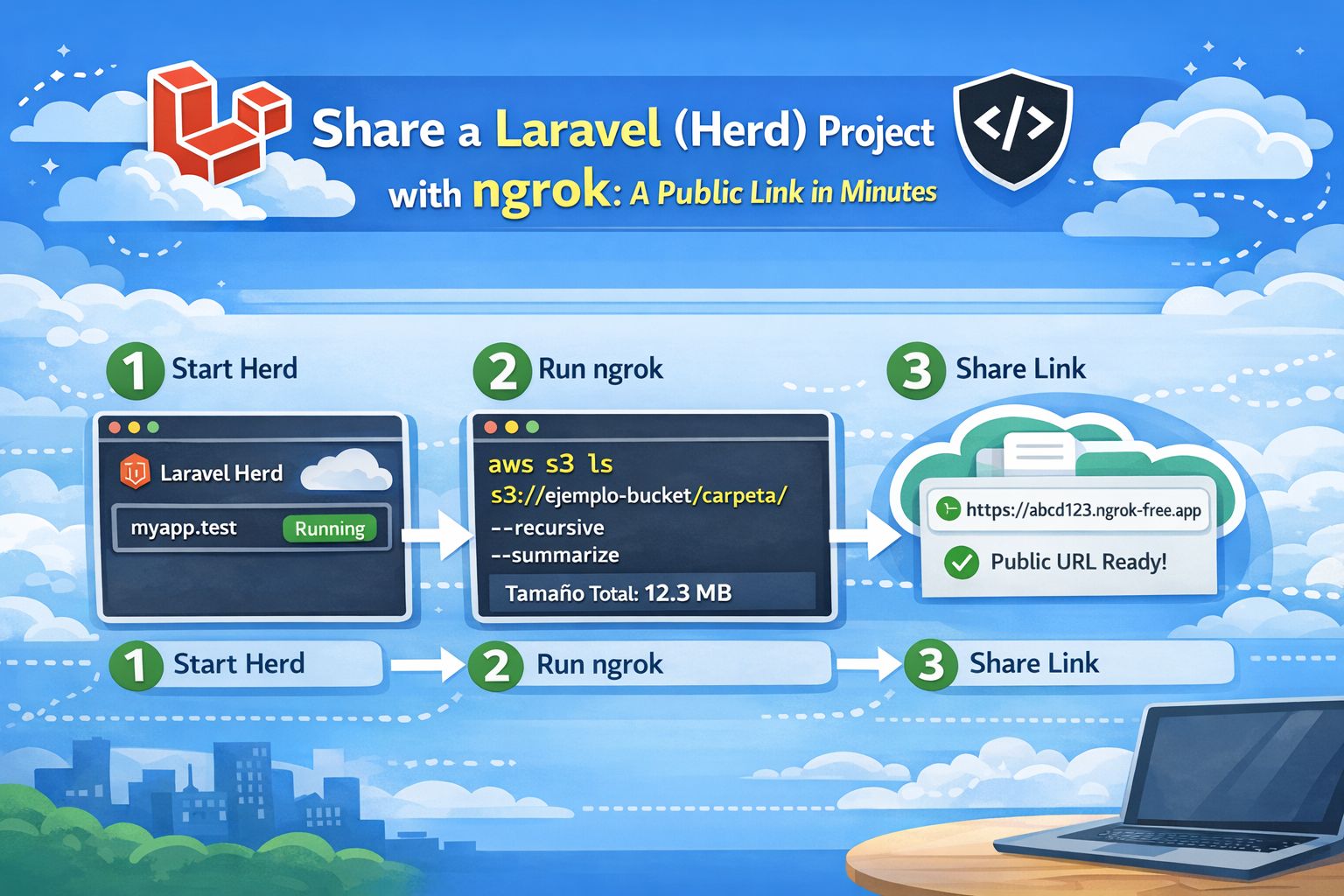
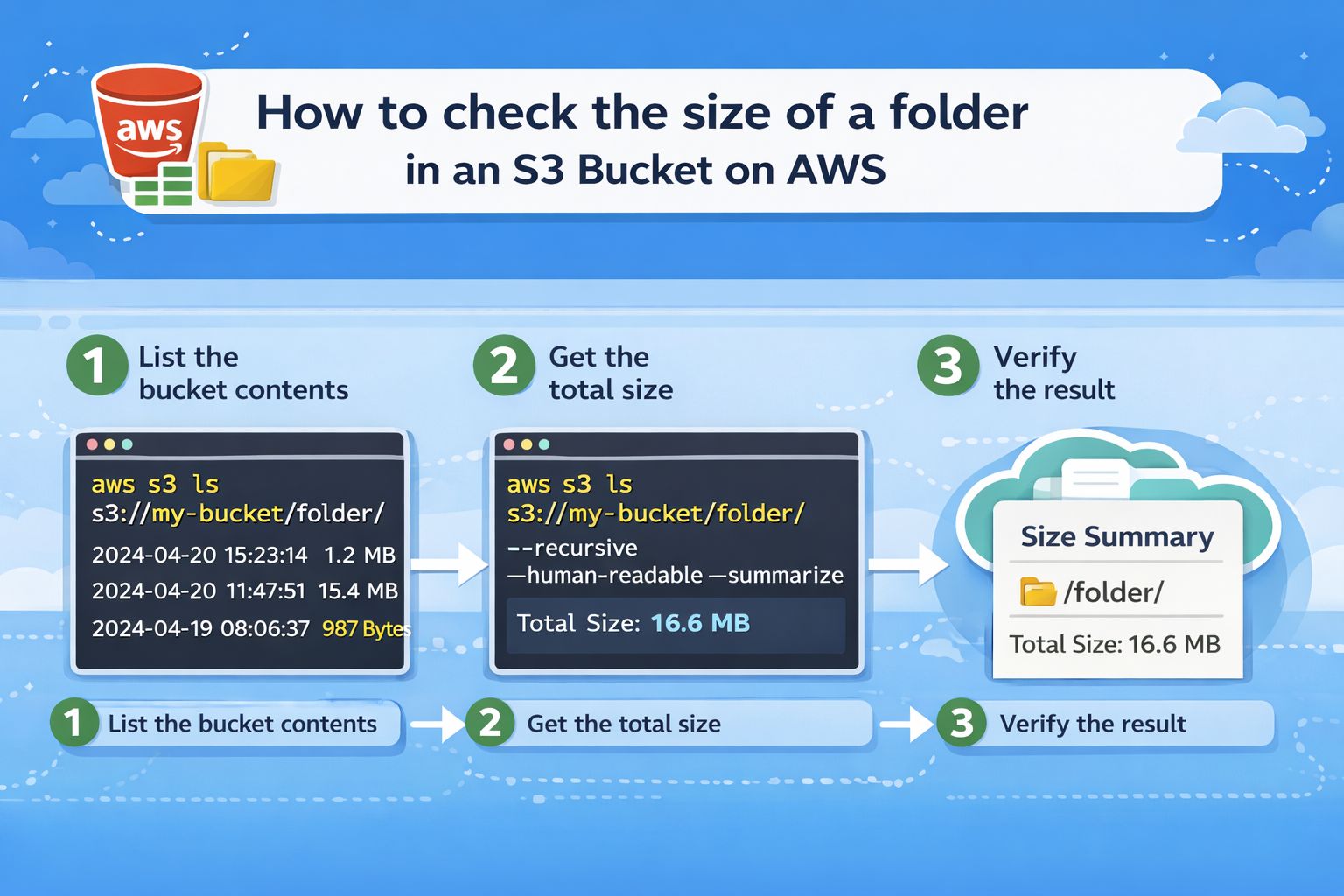
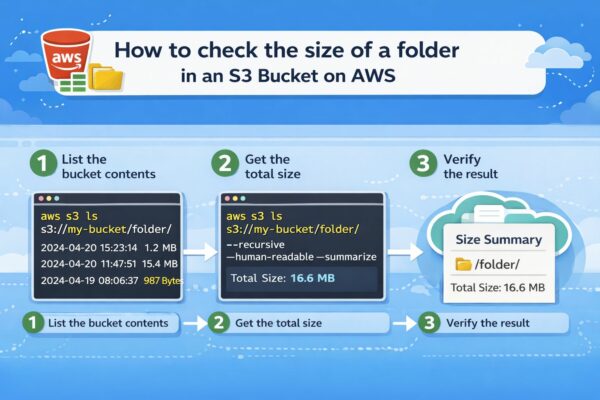
How to Calculate the Size of an S3 Folder Using AWS CLI
How to Calculate the Size of an S3 Folder Using AWS CLI Calculating the size [...]
Feb
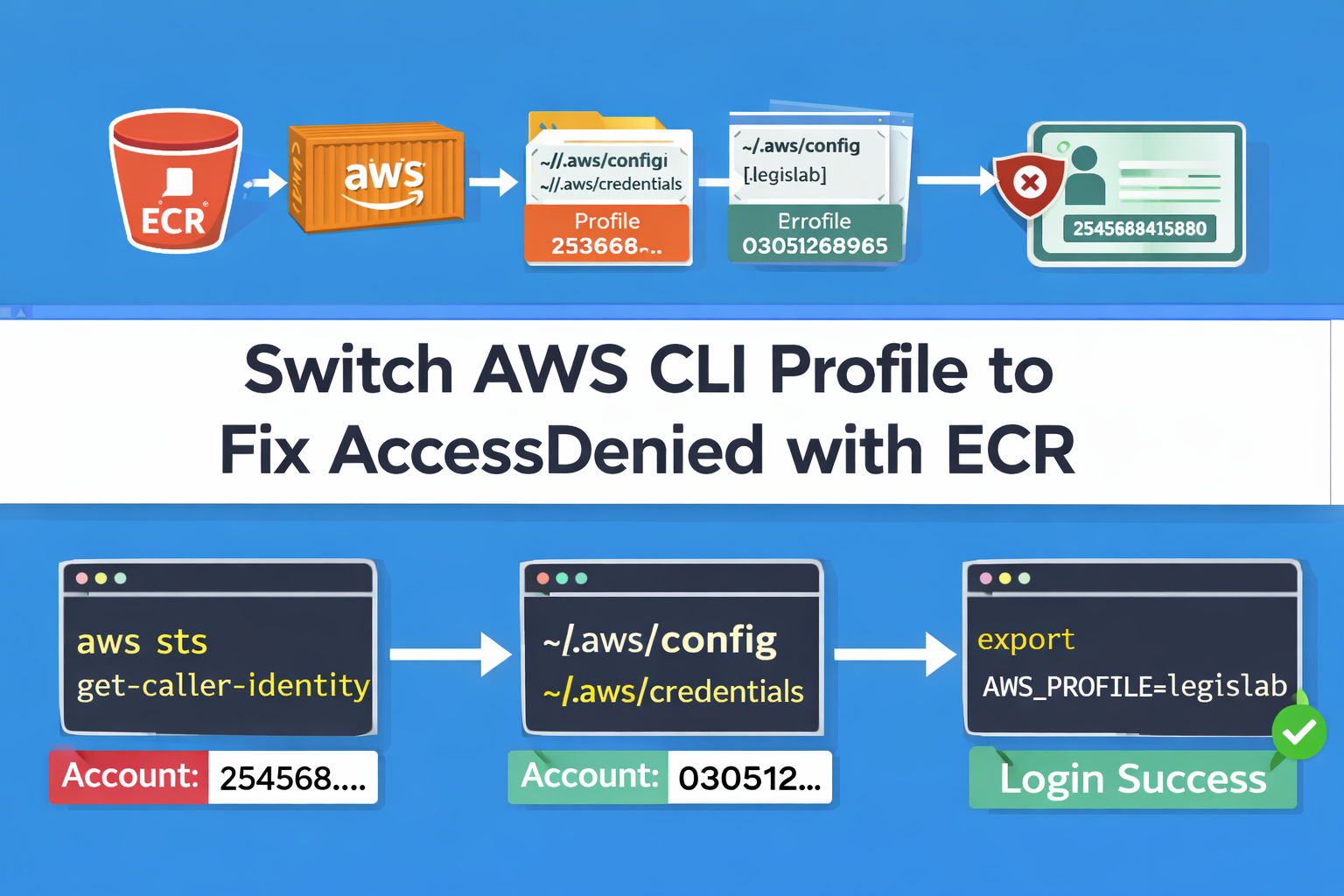
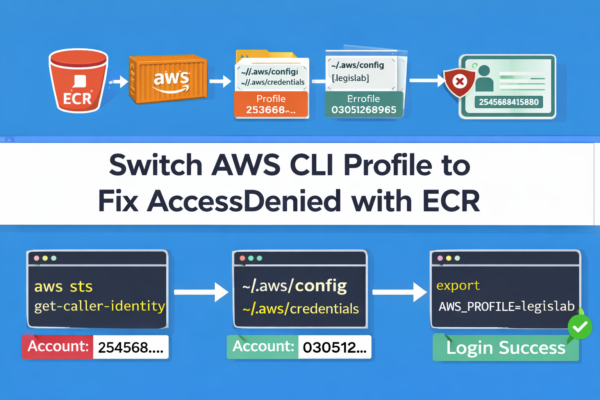
How to switch AWS CLI user/account (profiles) and fix “AccessDenied” in ECR
How to switch AWS CLI user/account (profiles) and fix “AccessDenied” in ECR If you use [...]
Feb
How to Install VirtualBox 2020
Go to the official Virtual Box website: https://www.virtualbox.org/wiki/Downloads Download the one for your OS where [...]
May
How to Connect to PostgreSQL (psql) from Your Local Computer to an AWS RDS
Connecting to an Amazon Web Services (AWS) RDS database from your local computer is an [...]
May
How to Deploy a React App on AWS S3 and CloudFront
In this tutorial, you will learn how to deploy a React application on AWS using [...]
May
Tutorial: Deploying an AWS Lambda Function with Dependencies, Environment Variables, and Refresh Token Using the AWS Console
1. Create the function in AWS Lambda Step 1: Access the Lambda console Step 2: [...]
May
Missing a Temporary Directory’ Error in WordPress: Causes and Solution on Servers with VestaCP
Below you will find a step-by-step tutorial to fix the “Missing a Temporary Folder” error [...]
May

 Español
Español