Remote Code Execution Risk Found in Cursor AI Editor — Vulnerability Highlights AI Supply Chain Threats
Security researchers have uncovered a high-severity vulnerability in the AI-powered code editor Cursor, potentially enabling [...]
Aug
Google Fixes Critical Android Flaws — Update Your Device Now
Google has released its August 2025 Android Security Bulletin, which includes patches for six vulnerabilities, [...]
Aug
$1 Million Up for Grabs: Pwn2Own Challenges Hackers to Break WhatsApp Without a Click
Security researchers will soon gather in Cork, Ireland, for one of the most anticipated cybersecurity [...]
Aug
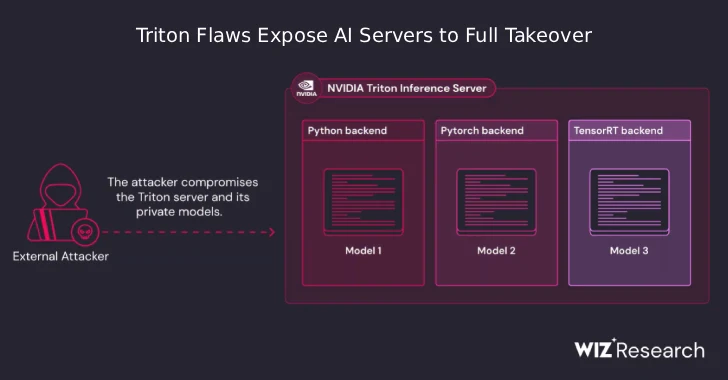
Critical NVIDIA Triton Server Vulnerabilities Could Let Hackers Hijack AI Infrastructure
A series of newly identified security flaws in NVIDIA’s open-source Triton Inference Server for Windows [...]
Aug
AI Web Usage Surge Reshapes Global Internet Traffic Trends
The rapid adoption of AI technologies is significantly reshaping global internet traffic patterns. A recent [...]
Aug
Massive Data Breach at Northwest Radiologists Affects Over 350,000 Residents
Northwest Radiologists, a medical imaging provider based in Bellingham, Washington, has confirmed a major data [...]
Aug
OpenAI Disables “Discoverable Chats” Feature in ChatGPT
OpenAI has quietly discontinued an experimental option in ChatGPT that let users make their conversations [...]
Aug
Threat Actors Exploit Fake OAuth Apps with Tycoon Kit to Compromise Microsoft 365 Accounts
A newly identified cyberattack campaign is raising serious concerns among security professionals. Threat actors are [...]
Aug
Google Chrome Introduces Store Reviews to Help Users Spot Legit Retailers
Online shopping just got a little safer, thanks to a new feature in Google Chrome [...]
Aug
Hackers Target Vulnerabilities Weeks Before Public Disclosure, Report Warns
A recent study from GreyNoise reveals a concerning trend in cyberattacks: threat actors are actively [...]
Aug

 Español
Español