Critical RCE Vulnerability Found in Cisco Secure Firewall Management Software
August 15, 2025 — Cisco has announced a severe security flaw in its Secure Firewall [...]
Aug
Zero Trust and AI: Redefining Privacy in the Era of Autonomous Agents
August 15, 2025 — Traditional views of privacy focused on control: walls, permissions, and access [...]
Aug
Italian Hotels Compromised, Tens of Thousands of Guest IDs Stolen and Sold Online
August 15, 2025 — Italy’s Computer Emergency Response Team (CERT-AGID) has issued a warning after [...]
Aug
U.S. Targets Garantex and Grinex Over $100M in Illicit Crypto Transactions Linked to Ransomware
August 15, 2025 — The U.S. Department of the Treasury’s Office of Foreign Assets Control [...]
Aug
Tight Budgets Push Cybersecurity Toward AI-Driven Automation
With financial constraints weighing heavily on cybersecurity teams, organizations are increasingly leaning on AI-powered automation [...]
Aug
Researchers Demonstrate Passkey Login Bypass Through WebAuthn Manipulation
Security researchers at SquareX, an enterprise browser security firm, have revealed a method that allows [...]
Aug
KernelSU v0.5.7 Vulnerability Allows Android Apps to Gain Root Privileges
Cybersecurity researchers have uncovered a critical flaw in KernelSU version 0.5.7 that could allow malicious [...]
New Android Malware Wave Targets Banking Customers with NFC Relay, Call Hijacking, and Root Exploits
Cybersecurity researchers have uncovered a new wave of Android malware, dubbed PhantomCard, which exploits near-field [...]
Aug
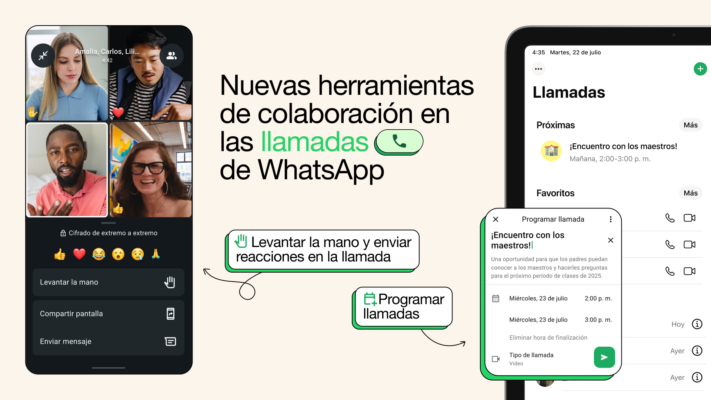
WhatsApp Introduces New Features for Smarter and More Interactive Group Calls
WhatsApp has rolled out new capabilities aimed at making group calls easier to schedule and [...]
Aug
Hackers Leverage CrossC2 to Bring Cobalt Strike Beacon to Linux and macOS
August 14, 2025 – Japan’s Computer Emergency Response Team Coordination Center (JPCERT/CC) has disclosed a [...]
Aug

 Español
Español