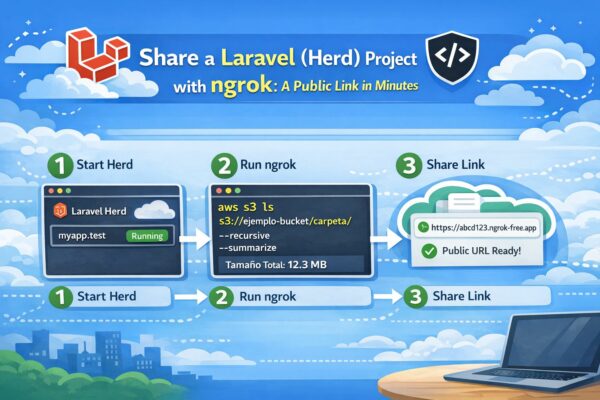
Share a Laravel (Herd) project with ngrok: a public link in minutes
Share a Laravel (Herd) project with ngrok: a public link in minutes If you’re running [...]
Feb
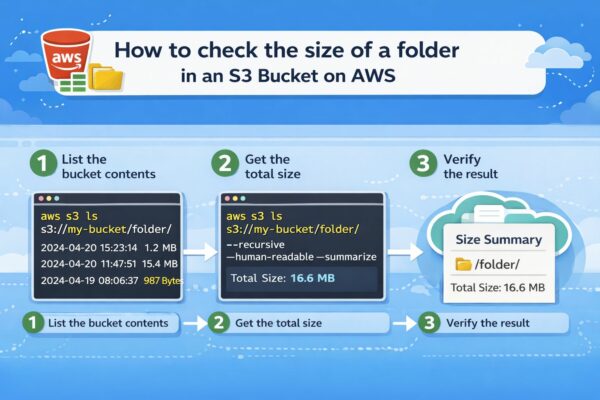
How to Calculate the Size of an S3 Folder Using AWS CLI
How to Calculate the Size of an S3 Folder Using AWS CLI Calculating the size [...]
Feb
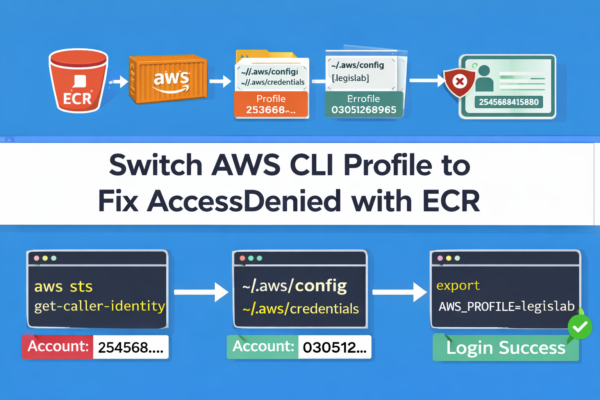
How to switch AWS CLI user/account (profiles) and fix “AccessDenied” in ECR
How to switch AWS CLI user/account (profiles) and fix “AccessDenied” in ECR If you use [...]
Feb
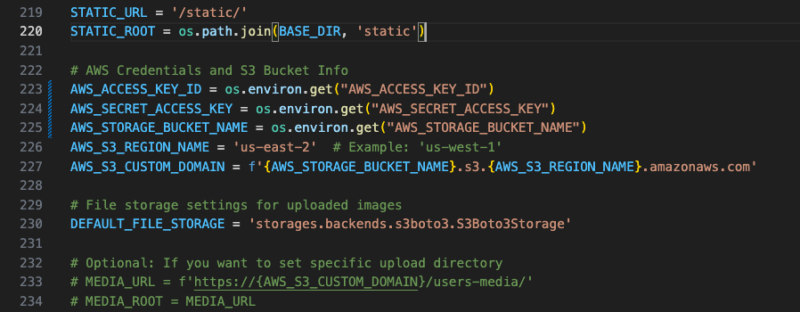
How to Securely Connect Django to AWS S3 — Two Recommended Approaches — Secure Setup Guide
When deploying Django apps on AWS, securely managing your access to S3 is critical. Hardcoding [...]
Jun
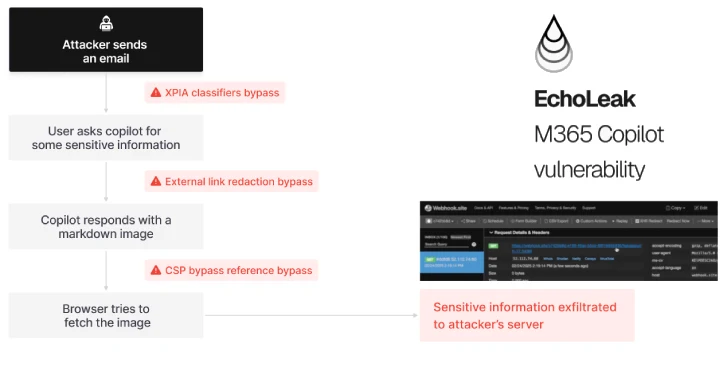
EchoLeak: Critical Zero-Click Vulnerability in Microsoft 365 Copilot Exposes Sensitive Data Without User Interaction
A newly discovered threat called EchoLeak has been classified as a zero-click vulnerability affecting Microsoft [...]
Jun
AI Becomes a Key Player in Spam and Scam Email Campaigns
More than half of today’s spam and malicious emails are now being generated by artificial [...]
Jun
Hydra WordPress Brute Force Attack
In this tutorial, I will explain in detail how to perform a brute force attack [...]
May
What is Phishing?
Phishing, as its name suggests, is literally information fishing. When we talk about a cyber [...]
May
What is Ngrok and How to Install It?
Ngrok is a service or tool that allows you to turn your local server into [...]
May

 Español
Español