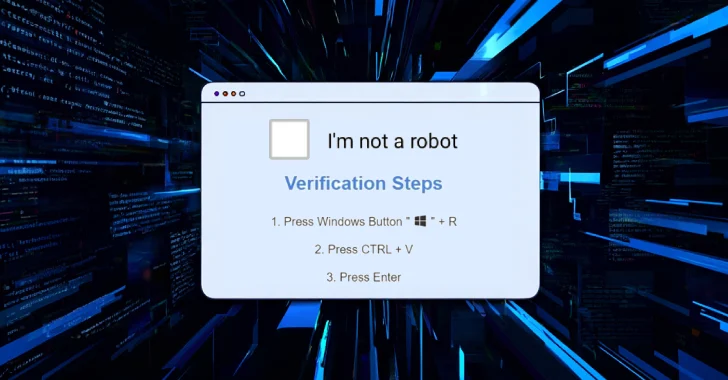
Cybercriminals continue to refine their social engineering tactics, with recent campaigns leveraging fake CAPTCHA pages and a technique known as ClickFix to deliver a powerful backdoor called CORNFLAKE.V3.
ClickFix: A Deceptive Initial Access Strategy
Researchers from Google-owned Mandiant have been tracking this activity under the designation UNC5518. The group uses fake CAPTCHA pages to lure victims into executing malicious commands, ultimately providing initial access that is later monetized by other threat actors.
The ClickFix infection vector prompts users on compromised websites to copy and execute a malicious PowerShell script through the Windows Run dialog box. This grants attackers the foothold needed to launch subsequent stages of the attack.
Multi-Group Operations and Payload Deployment
The access broker UNC5518 appears to collaborate with at least two other groups:
- UNC5774 – A financially motivated actor that deploys CORNFLAKE to deliver additional payloads.
- UNC4108 – A group with unclear motives, using PowerShell to distribute tools such as VOLTMARKER and NetSupport RAT.
The attack chain often begins with a victim reaching a fake CAPTCHA page via poisoned search engine results or malicious ads. Once tricked into running the malicious script, the victim downloads and executes CORNFLAKE.V3 from a remote server.
Inside CORNFLAKE.V3
CORNFLAKE.V3, observed in both JavaScript and PHP variants, enables attackers to:
- Execute multiple payload types (executables, DLLs, scripts, PowerShell commands).
- Collect and exfiltrate system information.
- Use Cloudflare tunnels to proxy traffic and evade detection.
Unlike its predecessor CORNFLAKE.V2, which was limited to downloading payloads, version V3 introduces persistence through Windows Registry modifications and supports more diverse payload types. Delivered malware often includes:
- Active Directory reconnaissance tools
- Credential harvesting scripts (Kerberoasting)
- WINDYTWIST.SEA, a backdoor capable of relaying TCP traffic, reverse shells, and lateral movement.
Mitigation Strategies
To counter this threat, security experts recommend:
- Disabling the Windows Run dialog box where possible.
- Conducting regular phishing and malware simulation exercises.
- Maintaining robust logging and monitoring systems to quickly detect malicious payload execution.
USB-Based Infections Deliver Cryptocurrency Miners
Alongside CORNFLAKE.V3 activity, Mandiant uncovered an ongoing USB-based campaign spreading since September 2024. Attackers leverage infected USB drives to deploy malware and cryptocurrency miners such as XMRig.
The infection typically unfolds as follows:
- The victim executes a malicious Windows shortcut (LNK) on the USB drive.
- This triggers a VBScript, which then launches a batch file.
- A chain of payloads follows, including:
- DIRTYBULK – A DLL launcher.
- CUTFAIL – A malware dropper that installs components like HIGHREPS and PUMPBENCH.
- HIGHREPS – Ensures persistence and additional downloads.
- PUMPBENCH – A backdoor enabling reconnaissance, remote access, and miner deployment.
- XMRig – Open-source mining software for Monero, Dero, and Ravencoin.
By replicating itself onto additional USB drives, PUMPBENCH facilitates continuous spread across environments, highlighting the persistent risk of removable media as an infection vector.
Final Thoughts
These campaigns underline how cybercriminals blend social engineering, backdoor persistence, and removable media infections to maximize their reach. Organizations should prioritize user awareness training, endpoint monitoring, and strict removable media controls to stay ahead of evolving threats like CORNFLAKE.V3 and USB-based malware infections.
Source: https://thehackernews.com/2025/08/cybercriminals-deploy-cornflakev3.html

 Español
Español