Cybersecurity researchers have uncovered a new ransomware strain called HybridPetya, which resembles the infamous Petya/NotPetya but introduces a dangerous twist: the ability to bypass the Secure Boot mechanism in UEFI systems by exploiting a vulnerability disclosed earlier this year.
The Slovak cybersecurity company ESET reported that malware samples were uploaded to VirusTotal in February 2025. According to researcher Martin Smolár, HybridPetya encrypts the Master File Table (MFT) — the structure that stores critical metadata about files on NTFS partitions. Unlike its predecessor, HybridPetya can target modern UEFI-based systems by deploying a malicious EFI application onto the EFI System Partition (ESP).
Bootkit and Installer Components
HybridPetya operates through two main components: a bootkit and an installer. The installer deploys the bootkit, which manages configuration, checks encryption status, and operates with three flags:
- 0 — ready to encrypt
- 1 — already encrypted
- 2 — ransom paid, disk decrypted
When set to 0, the bootkit updates the flag to 1 and encrypts the file \EFI\Microsoft\Boot\verify using the Salsa20 algorithm, then creates a file \EFI\Microsoft\Boot\counter to track encrypted disk clusters before beginning the encryption of NTFS partitions.
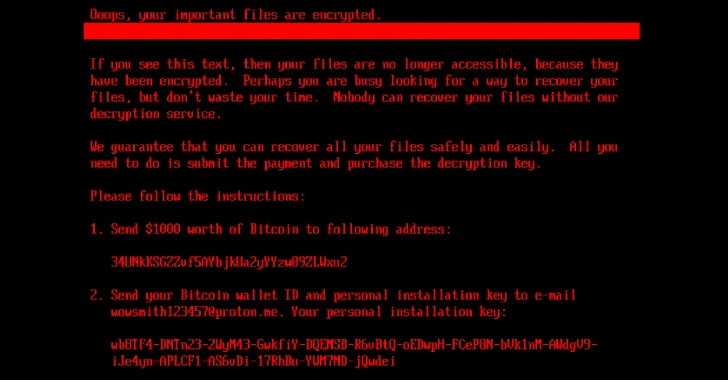
During this process, the malware shows a fake CHKDSK message on the victim’s screen, making it appear as though the system is repairing disk errors when in fact data is being encrypted.
If the disk is already encrypted (flag = 1), the victim is shown a ransom note demanding $1,000 in Bitcoin. Victims can then enter a “decryption key” provided after payment, which the bootkit verifies before initiating decryption, restoring legitimate bootloaders (\EFI\Boot\bootx64.efi and \EFI\Microsoft\Boot\bootmgfw.efi) from backups and prompting a reboot.
Bootloader changes introduced by HybridPetya cause a Blue Screen of Death (BSoD), ensuring the bootkit binary executes at startup.
Exploiting CVE-2024-7344
Select HybridPetya variants exploit CVE-2024-7344 (CVSS 6.7), a remote code execution flaw in the Howyar Reloader UEFI application (reloader.efi). Attackers rename the file to mimic a legitimate bootloader (bootmgfw.efi) and deploy a specially crafted cloak.dat file that contains the XORed bootkit binary.
When executed, reloader.efi searches for cloak.dat on the EFI partition and loads the malicious binary without integrity checks, effectively bypassing UEFI Secure Boot. Microsoft revoked the vulnerable binary in its January 2025 Patch Tuesday update.
Differences From NotPetya
Unlike the destructive NotPetya, HybridPetya is designed to allow operators to reconstruct decryption keys from victims’ installation data. ESET notes there is no evidence yet of HybridPetya being deployed in real-world attacks and suggests it could still be a proof-of-concept (PoC).
This makes HybridPetya at least the fourth known UEFI bootkit capable of Secure Boot bypass, following BlackLotus, BootKitty, and the Hyper-V backdoor PoC — proof that such bypasses are becoming more common and attractive to both attackers and researchers.
Security Implications and Recommendations
HybridPetya highlights the growing risks of ransomware campaigns that target UEFI and Secure Boot mechanisms, enabling attackers to gain persistence and control even before the operating system loads. To mitigate these risks, organizations should:
- Apply firmware and software patches promptly, including Microsoft’s revocations of vulnerable binaries.
- Restrict and monitor EFI partition access, detecting changes to bootloaders and EFI files.
- Enable observability at boot level to identify suspicious modifications or abnormal startup behavior.
- Maintain secure offline backups and validate recovery procedures regularly.
- Harden edge devices and enforce segmentation, limiting exposure to malicious EFI deployments.
⚡ This evolution of ransomware shows how attackers are moving beyond traditional malware delivery to compromise systems at the firmware level. Organizations must strengthen endpoint hardening, observability, and incident response strategies to stay ahead of emerging threats.
Source: https://thehackernews.com/2025/09/new-hybridpetya-ransomware-bypasses.html

 Español
Español