Echo Chamber: The Sophisticated Jailbreak Method Exploiting AI Language Models
Cybersecurity researchers are warning about a new and dangerously effective technique to bypass the safety [...]
Jun
XDigo Malware Exploits Windows LNK Vulnerability in Targeted Attacks Across Eastern Europe
Cybersecurity analysts have identified a new strain of Go-based malware, named XDigo, actively used in [...]
Jun
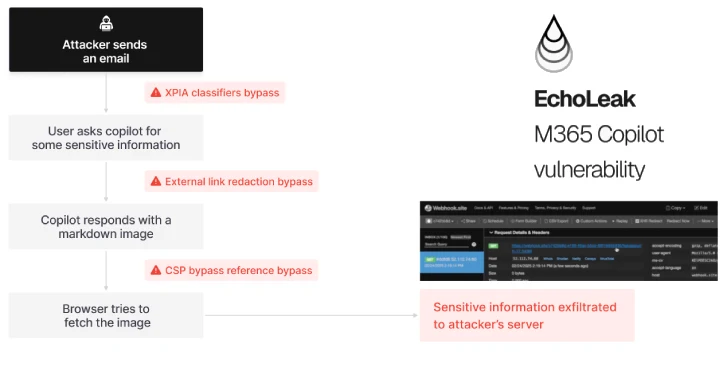
EchoLeak: Critical Zero-Click Vulnerability in Microsoft 365 Copilot Exposes Sensitive Data Without User Interaction
A newly discovered threat called EchoLeak has been classified as a zero-click vulnerability affecting Microsoft [...]
Jun
Achieve Your Goals with Habits
Achieve all your goals with Habits. A true gem. A FREE app available for IOS [...]
May
Why is Endpoint Protection CRUCIAL for Your Company?
Did you know that Mexico, behind Brazil, is the 2nd country with the most cyberattacks [...]
May
Best Practice for Updating the DOM in React After Making an HTTP POST Request
Below is a fairly detailed tutorial (in Spanish) that explains the before (how it used [...]
May

 Español
Español