Chinese Cyberespionage Group RedNovember Targets Global Defense and Government Organizations
Cybersecurity firm Recorded Future has reported that a Chinese cyberespionage group, known as RedNovember, has [...]
Sep
Malicious AI Agent Server Found Exfiltrating Emails
Security researchers from Koi Security have uncovered a malicious update in a widely used Model [...]
Sep
Neon App Pays Users to Record Calls, Selling Data to AI Firms
A new social networking app called Neon Mobile has risen to become the No. 2 [...]
Sep
Salesforce Patches “ForcedLeak” Vulnerability That Exposed CRM Data Through AI Prompt Injection
A newly disclosed critical security flaw in Salesforce’s Agentforce platform could have allowed attackers to [...]
Sep
New SVG-Based Phishing Attack Shows Why These Files Can Be Dangerous
Cybercriminals are once again exploiting SVG (Scalable Vector Graphics) files in a new phishing campaign [...]
Sep
Hackers Breach Boyd Gaming Systems
Boyd Gaming, a prominent casino and entertainment company, has reported a cybersecurity breach impacting some [...]
Sep
Cell Tower Hacking Equipment Seized Ahead of UN General Assembly
The U.S. Secret Service has recently dismantled a network of electronic devices capable of disrupting [...]
Sep
How One Weak Password Brought Down a 158-Year-Old Company
Most businesses struggle to survive beyond their fifth year—statistics show that around half of small [...]
Sep
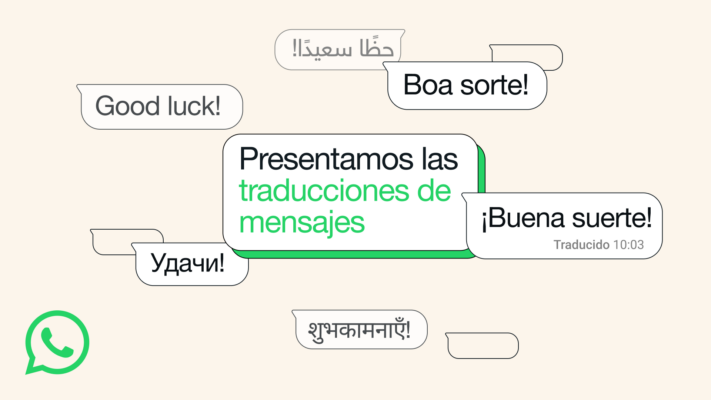
WhatsApp Rolls Out In-App Message Translation Feature
With more than 3 billion users across 180+ countries, WhatsApp continues to look for ways [...]
Sep
Police Deploying Drones as Flying License Plate Readers Raises Privacy Concerns
A recent report from the Electronic Frontier Foundation (EFF) warns that U.S. police departments are [...]
Sep

 Español
Español