6 Browser-Based Threats Security Teams Must Address Today
The frequency and sophistication of attacks targeting web browsers have surged dramatically in recent years. [...]
Sep
Samsung Fixes Critical Zero-Day Vulnerability Exploited on Android Devices
Samsung has rolled out its September 2025 security updates addressing a critical zero-day vulnerability that [...]
Sep
Phishing Campaigns Exploit RMM Tools for Covert Remote Access
Security researchers are warning about a wave of phishing campaigns that deploy remote monitoring and [...]
Sep
Apple Raises the Stakes for Spyware Makers with New iPhone Security Feature
Amid the buzz of new product launches, Apple quietly unveiled a security upgrade for its [...]
Sep
AI-Powered “Villager” Pentest Framework Hits 11K PyPI Downloads, Raising Abuse Worries
A newly released AI-driven penetration-testing framework called Villager has amassed nearly 11,000 downloads on the [...]
Sep
Critical Vulnerability in DELMIA Apriso Factory Software Exploited in Attacks
Cybersecurity authorities have raised alarms over a critical vulnerability affecting DELMIA Apriso, a widely used [...]
Sep
France Reports Apple Warned Users About New Spyware Attacks
According to the French government, Apple has alerted several individuals that their devices may have [...]
Sep
Attackers Adopt Novel LOTL Techniques to Evade Detection
Threat actors are increasingly chaining living-off-the-land (LOTL) techniques and abusing less obvious file types to [...]
Sep
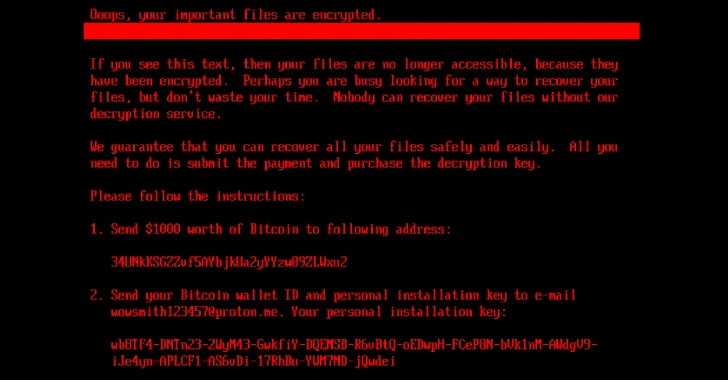
New HybridPetya Ransomware Bypasses UEFI Secure Boot via CVE-2024-7344
Cybersecurity researchers have uncovered a new ransomware strain called HybridPetya, which resembles the infamous Petya/NotPetya [...]
Sep
From a Simple “Like” to Financial Ruin: A Real-Life Scam Story
We often hear about people falling victim to scams, losing money, and facing devastating consequences. [...]
Sep

 Español
Español