Amazon has announced that it successfully identified and disrupted a watering hole campaign attributed to the Russia-linked threat group APT29, known for its longstanding role in state-sponsored cyber espionage.
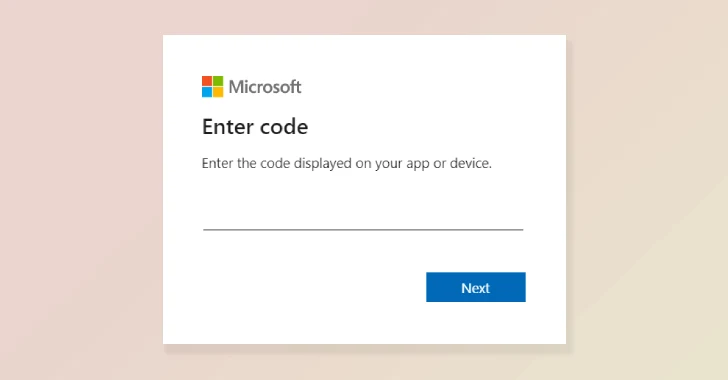
According to CJ Moses, Amazon’s Chief Information Security Officer, the campaign leveraged compromised websites that redirected unsuspecting visitors to attacker-controlled infrastructure. The goal was to trick users into authorizing malicious devices through Microsoft’s device code authentication flow, ultimately granting APT29 unauthorized access to sensitive accounts.
Who is APT29?
APT29 — also tracked as BlueBravo, Cozy Bear, Cloaked Ursa, Earth Koshchei, ICECAP, Midnight Blizzard, and The Dukes — is widely believed to operate under Russia’s Foreign Intelligence Service (SVR).
The group has a history of high-profile espionage campaigns. In recent months, it has been tied to:
- Attacks using malicious Remote Desktop Protocol (RDP) configuration files to target Ukrainian organizations.
- Phishing techniques, including device code phishing and device join phishing, to steal Microsoft 365 credentials.
- A June 2025 campaign reported by Google, where attackers abused application-specific passwords to infiltrate victims’ Gmail accounts, attributed to cluster UNC6293.
Amazon’s Findings
Amazon’s threat intelligence team revealed that APT29 compromised legitimate websites and injected malicious JavaScript that redirected around 10% of visitors to fake domains such as findcloudflare[.]com. These domains mimicked Cloudflare’s verification pages to create a sense of authenticity.
Victims were ultimately deceived into entering a valid device code — generated by the attackers — into Microsoft’s login portal, effectively granting APT29 full access to their accounts and data. This method, first outlined by Microsoft and Volexity in February 2025, highlights the group’s persistent use of identity-based phishing tactics.
Evasion Techniques
The campaign incorporated several methods to avoid detection, including:
- Base64 encoding to obscure malicious code.
- Cookies to limit repeated redirects and remain stealthy.
- Rapid infrastructure changes, shifting to new domains and cloud providers when blocked.
Despite APT29’s attempts to relocate its operations, Amazon stated that its teams continued tracking and disrupting their infrastructure. The attackers even moved away from AWS to another provider, but Amazon still observed them registering new domains such as cloudflare.redirectpartners[.]com to continue their phishing attempts.
Why It Matters
This latest campaign emphasizes APT29’s ongoing strategy of scaling its operations while refining its tradecraft. By abusing authentication workflows instead of traditional malware payloads, the group continues to pose a significant identity security risk for organizations worldwide.
As Moses noted:
“This opportunistic approach illustrates APT29’s continued evolution in scaling their operations to cast a wider net in their intelligence collection efforts.”
Source: https://thehackernews.com/2025/08/amazon-disrupts-apt29-watering-hole.html

 Español
Español