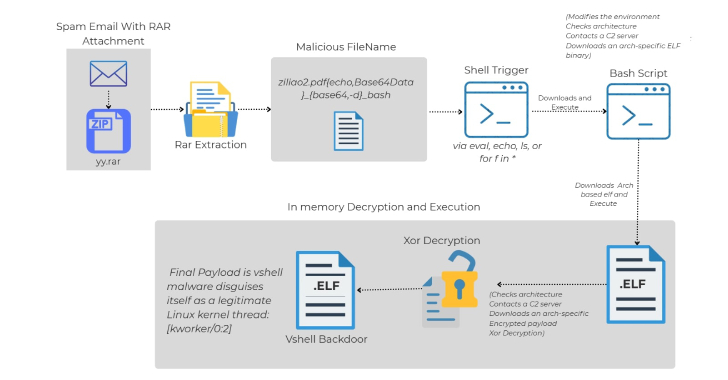
Cybersecurity researchers have identified a sophisticated Linux malware delivery method that leverages phishing emails and cleverly crafted file names within RAR archives to bypass traditional antivirus detection. The malware, known as VShell, is a Go-based remote access tool widely used by threat actors in recent years.
According to Trellix researcher Sagar Bade, the attack begins with a spam email containing a RAR archive. Uniquely, the malicious payload is not hidden inside the file contents or a macro—it is encoded directly in the file name. By exploiting shell command injection and Base64-encoded Bash scripts, the malware is triggered automatically when the shell interprets the file name.
This method is particularly dangerous because antivirus engines typically do not scan file names, allowing the malware to evade detection. The RAR attachment, often disguised as a survey invitation for a beauty product, distracts recipients while containing a filename designed to execute a Base64 downloader. This downloader then retrieves an ELF binary appropriate for the victim’s Linux architecture (x86_64, i386, i686, armv7l, or aarch64). The binary establishes communication with a command-and-control (C2) server to obtain, decrypt, and execute the VShell payload entirely in memory.
VShell offers full remote access capabilities, including reverse shell, file manipulation, process management, port forwarding, and encrypted C2 communications. Its in-memory execution makes it extremely difficult to detect using traditional disk-based security tools, and it can target a broad range of Linux systems.
The attack demonstrates an evolution in Linux malware delivery, where a seemingly innocuous filename within a RAR archive can serve as an automatic malware trigger. It exploits command injection in shell loops, leverages Linux’s permissive execution environment, and ultimately delivers a powerful backdoor capable of complete system compromise.
This discovery aligns with other recent Linux-focused threats. Picus Security recently analyzed RingReaper, a post-exploit tool that uses the Linux kernel’s io_uring interface to bypass monitoring and minimize detection. RingReaper enumerates system processes, network connections, and logged-in users while avoiding standard system calls frequently monitored by security tools, further illustrating the increasing sophistication of Linux-targeted malware.
Key Takeaways for Security Teams:
- Monitor and validate all email attachments, even seemingly harmless RAR files.
- Consider implementing stricter shell input validation to reduce risks from filename-based attacks.
- Deploy memory-based detection and advanced monitoring for Linux endpoints, as in-memory malware may bypass traditional antivirus solutions.
- Stay informed about emerging Linux threats like VShell and RingReaper to proactively strengthen defenses.
Si quieres, puedo hacer también una versión más resumida y directa enfocada en consejos prácticos para empresas, ideal para lectores que buscan información rápida sobre seguridad en Linux. Esto suele funcionar muy bien en blogs corporativos de ciberseguridad.
Source: https://thehackernews.com/2025/08/linux-malware-delivered-via-malicious.html

 Español
Español