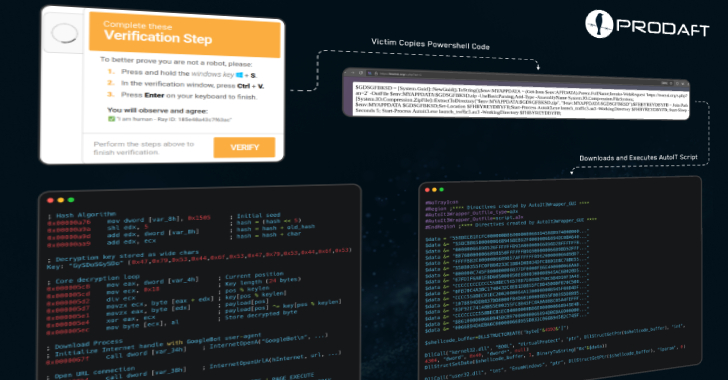
A newly identified malware loader named CastleLoader is rapidly becoming a favorite tool among cybercriminals, enabling them to deliver a range of information stealers and remote access trojans (RATs). According to a report by Swiss cybersecurity firm PRODAFT, CastleLoader is being actively used in campaigns that disguise themselves through fake GitHub repositories and ClickFix phishing attacks that mimic Cloudflare-related alerts.
A Modular and Evasive Threat
First observed in early 2025, CastleLoader is designed with a modular architecture, allowing it to serve both as an initial infection vector and a delivery platform for secondary malware. This separation between the loader and the final payload complicates detection and incident response, offering attackers greater flexibility and stealth.
The loader uses code obfuscation, runtime unpacking, and dead code injection to resist analysis. Once activated, it connects to a command-and-control (C2) server, downloads selected malicious modules, and executes them.
Some of the payloads delivered include:
- DeerStealer
- RedLine
- StealC
- NetSupport RAT
- SectopRAT
- Hijack Loader

Social Engineering and Phishing as Key Vectors
CastleLoader campaigns frequently use ClickFix techniques—tricking users into executing PowerShell commands by displaying fake error messages or CAPTCHA pages on domains impersonating software libraries, video conferencing platforms, or browser updates. These pages are often found through search engine results, making the phishing seem more legitimate.
In parallel, the malware spreads through fake GitHub repositories that imitate real software projects. Unsuspecting developers may download and install malware thinking they are using a trusted tool. This tactic exploits the high level of trust developers place in GitHub and highlights a growing risk within the open-source ecosystem.
Infection Scale and Infrastructure
Between May and July 2025, researchers tracked over 1,600 infection attempts across seven C2 servers, with at least 469 devices successfully compromised—an infection rate of nearly 29%.
The loader’s infrastructure includes a web-based control panel typical of malware-as-a-service (MaaS) operations, further confirming the professional nature of the threat actors involved. The use of sandbox evasion, PowerShell abuse, and GitHub impersonation places CastleLoader among the most advanced loaders currently in circulation.
Why It Matters
CastleLoader is not just another malware variant—it’s a scalable delivery framework capable of distributing a wide range of malicious tools. Its evolution marks a significant step in the development of malware loaders, emphasizing stealth, modularity, and effectiveness.
Organizations and developers should be extra vigilant:
- Avoid downloading code or tools from unverified GitHub repositories.
- Never execute unfamiliar PowerShell commands prompted by browser alerts.
- Monitor endpoints for unusual network activity, especially C2 traffic.
As CastleLoader continues to evolve and spread, it serves as a reminder of the increasing sophistication of modern cyberattacks—and the urgent need for proactive security measures.
Source: https://thehackernews.com/2025/07/castleloader-malware-infects-469.html

 Español
Español